A Comparative Analysis of Software Liability Policies
ABSTRACT

Fig. 1: Comparing the effects on security investment and social welfare for each of three policies: software security standards, liability on patching costs, and liability on zero-day losses. Panel (a) illustrates how each policy affects the equilibrium investment in security made by the vendor. Panel (b) illustrates the impact of each policy on social welfare.
I. INTRODUCTION
In the current network environment, there are serious incen- tive problems among various actors whose decisions impact the overall security of the cyber infrastructure; the risks associ- ated with attacks on this infrastructure are growing in number and potential impact; and the importance of the role of regu- lation is increasingly understood and debated (see, e.g., [1]- [4]). However, answering how regulation can actuate a shift toward preferable outcomes, such as an increasingly secure cyber infrastructure and higher social surplus associated with these public resources, is not well understood and requires formal analysis. We begin to explore this important question by analyzing an economic model that captures both security interdependence and the primary underlying incentives of actors.
One corrective means to address the underlying incentive problems which has received intense debate in the security community is the ownership of liability for network security losses. We investigate how liability policies can be used to increase Internet security considering the effects of intercon- nectivity and the resulting interdependence of users' security actions on one another. There are two economic factors, the roles of which we will be focusing on when we explore the
the impact of each policy on social
I. INTRODUCTION
In the current network environment, there are serious incentive problems among various actors whose decisions impact the overall security of the cyber infrastructure; the risks associated with attacks on this infrastructure are growing in number and potential impact; and the importance of the role of regulation is increasingly understood and debated (see, e.g., [1]- [4]). However, answering how regulation can actuate a shift toward preferable outcomes, such as an increasingly secure cyber infrastructure and higher social surplus associated with these public resources, is not well understood and requires formal analysis. We begin to explore this important question by analyzing an economic model that captures both security interdependence and the primary underlying incentives of actors.
One corrective means to address the underlying incentive problems which has received intense debate in the security community is the ownership of liability for network security losses. We investigate how liability policies can be used to increase Internet security considering the effects of intercon- nectivity and the resulting interdependence of users' security actions on one another. There are two economic factors, the roles of which we will be focusing on when we explore the effectiveness of the mechanisms. First, users who do not patch impose negative network externalities on other users - the larger the population of users who do not patch the software, the larger the network risk associated with vulnerabilities. Second, patching is a costly undertaking. If a vendor makes a patch available when there is a vulnerability and a user decides to patch her system, testing and installing that patch brings a cost burden on the user. Thus, many users do not patch their systems even if a patch is available (see, e.g., [5] and the references therein). Combining this behavior with the network effects discussed above, we see that the costliness of patching and negative security externalities increase the security risk faced by all users, hence, both the value of the software product for users and, consequently, social welfare are reduced.
II. APPROACH
In light of these factors, we construct a microeconomic model accounting for government, firm, and user incentives. Using this model, we begin by studying the economics of the network environment in a short-run setting, where the security level of the software is taken as given. In the long run, the role of liability on increasing Internet security also impacts the incentives of software providers to adjust the security quality
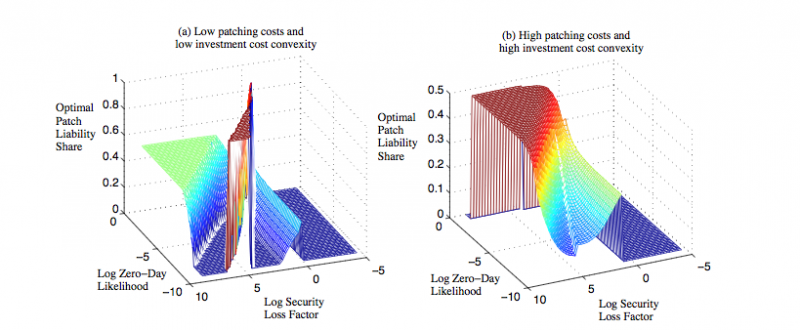
Fig. 2: A characterization of the optimal patch liability share as it depends on the likelihood of zero-day attacks and the potential magnitude of security losses.
of their products at the design and development stage. There- fore, we subsequently study a long-run setting where vendors can invest in security quality in response to policy. We analyze and contrast three classes of security liability policies, namely (i) Loss Liability Policies, where the software vendor is liable to partially or fully compensate users' losses incurred in case of a zero-day attack; (ii) Patch Liability Policies, where the software vendor is held liable to compensate patching costs incurred by users if a vulnerability is discovered before it is exploited; and (iii) Security Standards Policies, where regula- tion enforces a certain standard of security to be achieved by the vendor during software development to mitigate security vulnerabilities. The former two policies can be applicable in both short-run and long-run settings, while the last one is only applicable in the long run. We explore the role of zero-day attacks by studying and comparing these policies in two security environments, with low and high zero-day attack likelihood respectively. For each class of policies and each zero-day environment, we characterize the optimal policy and study its effectiveness. We then compare and contrast their effectiveness and generate policy recommendations based on our analysis. Our goal is to answer the question whether vendor security liability can be an effective method to improve security and the net social value generated by software, and, if so, how.
III. RESULTS
As can be seen in panel (b) of Fig. 1, a main takeaway from our analysis is that it is advisable to social planners to refrain from imposing loss liability on vendors of soft- ware with interdependent risks. We find that whether or not software vendors have the opportunity to invest in security in response to loss liability makes little difference in the net impact of such a policy: welfare mostly decreases. On the surface, one may think that holding the vendor liable for a portion of consumers' losses would provide increased incentives for the vendor to improve security, and, in some cases, the vendor's optimal investment indeed rises. However, even if investments positively respond, the vendor tends to restrict usage through pricing to limit its exposure to liability on these losses. Hence, loss liability is often an inefficient policy to apply in the software industry. On the other hand, we find that both patch liability and security standards should play an important role in software policy. Security standards are recommended for environments with low zero-day attack risk because, under these conditions, software vendors lack incentives to produce software that is sufficiently secure. On the other hand, sharing of patching costs is recommended for environments with higher zero-day attack risk because of its ability to increase security in riskier settings by incentivizing appropriate user behaviors. Fig. 2 illustrates how the optimal patching cost share (as prescribed by a social planner) varies with economic costs and security characteristics. There are many ways to implement the essence of a patch liability policy. For example, one could have software vendors offer customers who agree to adhere to an appropriate patching strategy with a price discount because patching behavior is verifiable in such interconnected environments.
ACKNOWLEDGMENTS
This material is based upon work supported by the National Science Foundation under Grant No. CNS-0954234.
REFERENCES
[1] M. Chertoff, "Remarks by Homeland Security Secretary Michael Chertoff at the Chamber of Commerce on cybersecurity," Office of the Press Secretary, Oct 2008.
[2] B. Krebs, "Bush approves cybersecurity strategy," Washington Post, Jan 2003.
[3] F. B. Schneider, "It depends on what you pay," IEEE Security & Privacy, vol. 3, no. 3, p. 3, 2005.
[4] J. Lewis, "Innovation and cybersecurity regulation," CircleID, Mar 2009. [5] T. August and T. I. Tunca, "Network software security and user incen- tives," Management Science, vol. 52, no. 11, pp. 1703-1720, 2006.
BIO
Terrence August is an assistant professor of Innovation, Technology and Operations Management at the Rady School of Management, University of California, San Diego. He received his Ph.D. from the Graduate School of Business at Stanford University in 2007. His research interests broadly span information systems and operations management, including the economics of network software, production and service management, pricing and policy associated with network goods, and the interaction of digital piracy and security risk.
Currently, as part of an NSF supported research project, he is examining the control of information security risk using economic incentives. Specifically, he aims to develop an understanding of the relationship between government policy, economic incentives of firms and consumers, and software security risks of networks by studying three important aspects: software liability, the impact of software deployment models, and open source software incentives for security.
Switch to experimental viewer