 User-Centered Design for Security - UMD - April 2015
User-Centered Design for Security - UMD - April 2015
Public Audience
PI(s): Jen Golbeck and Adam J. Aviv
Researchers: Yehuda Katz, Zahra Ashktorab, Dane Fichter, Jeanne Luning-Prak, Devon Budzitowski, Ryan Kelly, Mathew Sommers, Ethan Genco, Didar Alan, Kyle Hawkins
PROJECT OVERVIEW
Our goal is to better understand human behavior within security systems, and to use that knowledge to propose, design, and build better security systems. When humans are involved in security systems in any way, the usability is important. A system that is designed around natural human memory, attention, and cognitive abilities will be easy to use and lead people toward acting in secure ways; systems that force users into inherently difficult tasks lead to people circumventing security guidelines or protocols in order to get their tasks done efficiently.
In the first year of this project, we undertook several efforts in the usable security space; in particular in the space of understanding the security and usabily of text and graphical passwords. The concrete results of this research effort is the development of new classes (PI Golbeck), the sponsor of capstone projects (PI Aviv), the presentation and publication of papers (PI Golbeck and PI Aviv), and numerous service opportunities that bring awareness to usable security issues to a wider audience.
In this section, we detail our research efforts in the previous year for the following topic areas, which are all related to the hard problem of Human Behavior and Metrics:
- Improving Password Memorability
- Measuring Cueing Language in User Graphical Password Selection
- Understanding, Measuring and Applying User Perceptions of Security and Usability
- Privacy Conscious URL Sharing
We also outline how this research effort will continue in Year 2 with the expansion of new projects. One theme of this research project that will continue into Year 2 is the focus on usable security issues related to mobile devices. Clearly, as mobile devices, such as smartphones, tablets, etc., continue to proliferate as the primary computer for many individuals, understanding the usability and security impact remain a primary focus for this research effort.
Improving Password Memorability: This project is based around designing mechanisms to help people remember passwords more effectively. Password resets are a point of insecurity, so the more often people can remember passwords, the more reduced this risk point becomes. We have designed an experiment to test how well memorization techniques can be applied to passwords.
The core idea behind this work is that if people use a password enough, it will eventually become part of their long-term memory. There are various "schedules" that people use to memorize other things, like words for standardized tests such as the GRE or SAT. We are testing whether prompting people to recall a password on such a schedule can improve long term recall of the password.
We have designed and deployed a pilot test of this experiment. After that success, we revised the protocol and replaced a web-based interface with email reminders. We replaced that with an iPhone app called CrainTrain, which we developed, that is a generic tool for helping with memorization. We are using that app (Figure 1) to prompt people to recall their password on a schedule with decreasing frequency and to compare their accuracy rates with that for passwords where they were not prompted over time to help with memorization. Success with this experiment would suggest techniques for improving the rate at which people remember important password, minimizing resets and the associated risks.
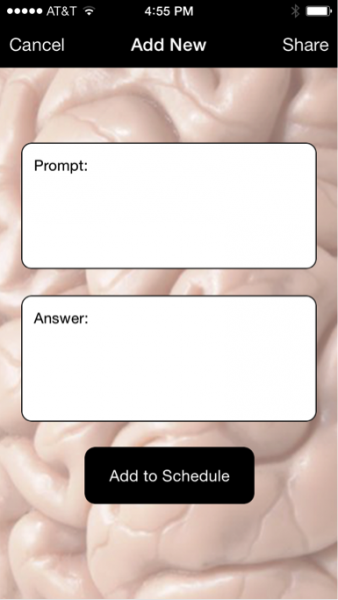
Figure 1: The CrainTrain screen where users enter a prompt ("What is your password") and answer (the actual password)
Measuring Cueing Language in User Graphical Password Selection. When users are asked to select passwords, they are asked to select a "strong" password, but how effective is this language as compared to other language choices, such as "unique" or "secure" or other visual or textual indicators that could be use prior to selecting a password? Current efforts in this domain are developing an empirical research methodology that can test hypotheses regarding user queuing and their eventual password selection, focusing first on graphical passwords and later extending to text based passwords. The results of this research will lead to the better design of security procedures, which could "nudge" users towards more secure choices.
At the end of Year 1, with efforts from research students Jeanne Lunig-Prak and Devon Budzitowski, we have developed a pilot study to be run on Amazon Mechanical Turk. The survey requires participants to select an initial graphical password which they will be then cued that that choice was insufficient in some way. A participate selects again after the cue, and the difference between these choices, and a later test of recall, informs us of how well the cueing works for different cue. This research effort will continue into Year 2.

Figure 2: A sample cue from pilot study on improving password choice
Understanding, Measuring and Applying User Perceptions of Security and Usability. This research focuses on using empirical studies (surveys) to understand perceptions of security and usability in visual systems. Current research has focused on the graphical password system used by Android, and a large dataset of pair-wise preferences has been collected. The next phase of the research is to apply what we have learned to predict user perceptions, and to use those predictions to design better policies, better user interfaces, and more-secure systems generally. The research goal is to design systems where users' perceptions of security match some known metric of security, thus inducing security by design.
This research effort has led to the publication and presentation of research at the 2014 Annual Computer Security Applications Conference (ACSAC’14). The research effort of Dane Fichter, an undergraduate student at Swarthmore College, led to the design of a large on-line survey where users chose between two graphical passwords to indicate a security preference. The findings of this research are that more spatial features, such as left vs. right shifting had little effect on perceptions, while more complex features, such as crosses, had a much large effect.
Following this research, we conducted two studies to better understand perceptions. Jeanne Luning-Prak, a summer high school intern during the summer of 2014, designed and launched a survey to have participants self-report their Android password patterns. The survey is ongoing, and over 700 individuals have completed the survey. Interesting, preliminary findings show that, in contrast to perceptions, users select patterns where shifting and shapes play a much larger roll. We hope to correlate this information with various demographic data collected during the survey as well as inquiries regarding privacy perceptions of mobile devices, generally. So far, a poster has been presented on this research at ACSAC’14, and a full paper is being prepared for submission over the summer of 2015.
Research student Devon Budzitowski (Fall’15) is leading a follow up study to see if the number of contact points in the grid (3x3 vs. 4x4) change the perceptions of security. We have designed an in-person survey where participants both choose graphical passwords of their own and try and guess other participants passwords. The study conducted with both 3x3 and 4x4 grid sizes provides a nice comparison point to understand both what participants are choosing for them selves, and what they believe others might choose. A poster is currently being prepared on this research to be presented at SOUPS’15, and a full paper is being prepared for submission over the summer of 2015.
As a new effort in this domain, a student capstone team at USNA has been investigating if the keyboard layout on mobile devices impacts password choice as well as the efficiency of password entry. Capstone students Ryan Kelly, Matthew Sommers, Ethan Genco, Didar Alam, and Kyle Hawkins have spent much of the Fall’14 and Spring’15 developing new keyboards for mobile devices that adjust the layout and provide user input during password selection. We have also developed a pilot study to measure the performance of the new keyboard, and this research will continue into Year 2. A poster is currently being prepared about this research effort to be presented at SOUPS’15.
Figure 3: A sample password entry keyboard which more promenantly displays special symbols and numbers to encourage their use and for increased efficiency
Privacy Conscious URL Sharing. A defining characteristic of current Internet culture is to share information, e.g., through social network services. Recent efforts by the PI have shown that URLs being shared may contain more content than intended by the users, in particular, information embedded within the URL query string. The URL query string stores additional key-value pairs that are used by the web server to faithfully render the resulting web page; however, not all query string keys and values are used for rendering. Some are used for user tracking, and if publicly shared, this tracking information is also shared. We strive to develop new systems that better analyze the privacy risks for users through new metrics, properly present those risks to users, and enable users to make choices about how their URLs are shared. The results of this research will improve the privacy understanding and privacy exposure of users.
This project was completed in collaboration with Andrew G. West, a research scientist at Versign Labs. We have published two papers on the topic during Year 1: one paper at the Workshop on Web 2.0 Security and Privacy (best paper winner), and a follow up journal version in IEEE Internet Computing Magazine. Unfortunately, this project is conlcuding and unlikely to continue into Year 2.
HARD PROBLEM(S) ADDRESSED
Human Behavior; Metrics.
SERVICE
Program Co-Chair service by Adam Aviv. 8th Workshop on Cyber Security Evaluation and Test (CSET’15).
Wireless Security Track Chair for IEEE VTC Fall 2015 service by Adam Aviv. IEEE Vehical Technoligy Conference.
Invited Talk at University of Maryland Baltimore County on “Human Factors in Mobile Device Authentication.” Jan 16, 2015.
Invited Talk at Carnegie Melon University on “Measuring Visual Perceptions of Security: Case study of Android’s Graphical Password” Jul 2, 2014.
Coursera MOOC "Usable Security" offered once in 2014, once in 2015. A total of 55,000 students registered for this course
Keynote Presentation by Jennifer Golbeck, "Privacy and Social Media", presented at Howard County Gifted Middle School Expo, May 29, 2015
Keynote Presentation by Jennifer Golbeck, "Data Analytics and Security" presented at Ingram Micro Vantage Kansas City, February 18, 2015.
Keynote Presentation by Jennifer Golbeck, "Toward Usable Security", presented at National Cyber Security Awareness Month, ATS, Inc.
PUBLICATIONS
Papers published for Y1
- Understanding Visual Perceptions of Usability and Security of Android's Graphical Password Pattern. Adam J. Aviv and Dane Fichter. Procedings of the 30th Annual Computer Security Applications Conference (ACSAC), 2014.
- Measuring Privacy Disclosures in URL Query Strings. Andrew G. West and Adam J. Aviv. Internet Computing, IEEE, 18(6): 52-59, 2014.
-
On the Privacy Concerns of URL Query Strings . Andrew G. West and Adam J. Aviv. Workshop on Web 2.0 Security and Privacy. May, 2014.
- A Self-Report Survey of Android Unlock Passwords. Jeanne Luning-Prak and Adam J. Aviv. Poster presentation at ACSAC 2014.
Papers submitted for publication
- SoK: Humans in security Systems. J. Golbeck, M. Mazurek, and C. Mayhorn. Submitted to IEEE Security & Privacy.
STUDENTS
Yehuda Katz, PhD Student – Summer '14
Zahra Ashktorab, PhD student - Fall'14 – Spring '15
Jeanne Lunig-Prak: high school intern in Summer'14/Fall'14 (returning Summer’15)
Devon Budzitowski: independent research student in Spring'15
Ryan Kelly: student capstone in Fall’14/Spring’15
Mathew Sommers: student capstone in Fall’14/Spring’15
Ethan Genco: student capstone in Fall’14/Spring’15
Didar Alan: student capstone in Fall’14/Spring’15
Kyle Hawkins: student capstone in Fall’14/Spring’15


