 Data Driven Security Models and Analysis - July 2015
Data Driven Security Models and Analysis - July 2015
Public Audience
Purpose: To highlight project progress. Information is generally at a higher level which is accessible to the interested public. All information contained in the report (regions 1-3) is a Government Deliverable/CDRL.
PI(s): Ravi Iyer
Co-PI(s): Zbigniew Kalbarczyk and Adam Slagell
Researcher(s): Cuong Pham, Zachary Estrada, and Phuong Cao
HARD PROBLEM(S) ADDRESSED
This refers to Hard Problems, released November 2012.
- Predictive security metrics – design, development, and validation
- Resilient architectures – in the end we want to use the metrics to achieve a measurable enhancement in system resiliency, i.e., the ability to withstand attacks
- Human behavior – data contain traces of the steps the attacker took, and hence inherently include some aspects of the human behavior (of both users and miscreants)
PUBLICATIONS
Papers published in this quarter as a result of this research. Include title, author(s), venue published/presented, and a short description or abstract. Identify which hard problem(s) the publication addressed. Papers that have not yet been published should be reported in region 2 below.
[1] P. Cao, E. Badger, Z. Kalbarczyk, R. Iyer, A. Slagell, “Preemptive Intrusion Detection: Theoretical Framework and Real-World Measurements,” 2nd Symposium and Bootcamp on the Science of Security, HotSoS 2015, April 21-22, 2015.
Abstract: This paper presents a Factor Graph based framework called AttackTagger for highly accurate and preemptive detection of attacks, i.e., before the system misuse. We use security logs on real incidents that occurred over a six-year period at the National Center for Supercomputing Applications (NCSA) to evaluate AttackTagger. Our data consist of security incidents that led to compromise of the target system, i.e., the attacks in the incidents were only identified after the fact by security analysts. AttackTagger detected 74 percent of attacks, and the majority them were detected before the system misuse. Finally, AttackTagger uncovered six hidden attacks that were not detected by intrusion detection systems during the incidents
[2] Z. J. Estrada, C. Pham, F. Deng, Z. Kalbarczyk, R. K. Iyer, L. Yan, “Dynamic VM Dependability Monitoring Using Hypervisor Probes,” to appear at 11the European Dependable Computing Conference- Dependability in Practice, EDCC 2015, Paris, France, Sept. 7-11, 2015.
Abstract: Many current VM monitoring approaches require guest OS modifications and are also unable to perform application level monitoring, reducing their value in a cloud setting. This paper introduces hprobes, a framework that allows one to dynamically monitor applications and operating systems inside a VM. The hprobe framework does not require any changes to the guest OS, which avoids the tight coupling of monitoring with its target. Furthermore, the monitors can be customized and enabled/disabled while the VM is running. To demonstrate the usefulness of this framework, we present three sample detectors: an emergency detector for a security vulnerability, an application watchdog, and an infinite-loop detector. We test our detectors on real applications and demonstrate that those detectors achieve an acceptable level of performance overhead with a high degree of flexibility.
ACCOMPLISHMENT HIGHLIGHTS
This quarter we focused on: (i) building a security testbed that provides an execution platform for replaying security attacks in a controlled environment and (ii) applying game theory with learning for cyber security monitoring.
1. Game Theory with Learning for Cyber Security Monitoring
We model multi-stage attacks as multi-stage security game and solve it using Q-Learning. A new attack model is derived from the study on incident data from the National Center of Supercomputing Applications (NCSA) to justify the use of reinforcement learning. The new model accommodates the limited observation of the defender on the attack model as discussed below.
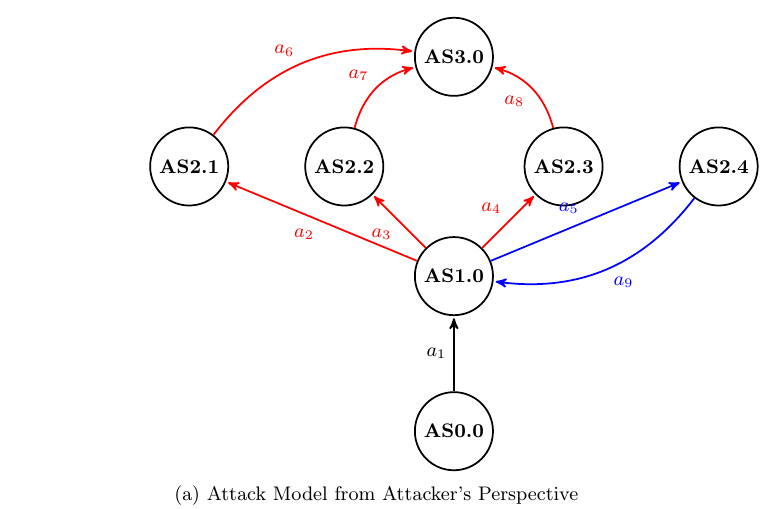

Figure 1: State Diagram Representations of the Attack Phase (a, b) and a Snapshot of the Security Game (c). Note that although (a) and (b) both represent the same attack, they have different numbers of states and actions, because the defender has a limited view of the attacker’s actions.
Attack Model. Figure 1a models an attack in four phases. AS0.0 is a base state. It is the default state, in which the attacker has not taken any malicious action. In this state, an attacker cannot be differentiated from a benign user. Using stolen credentials or already exploited backdoors, attackers gain access to the system, which leads to AS1.0. In AS1.0, the attacker has 4 options: to download malware (well-known, rare, or new) or download benign software. Downloading benign software would not give immediate benefit to the attacker, but we model it to represent a case in which the attacker is trying to obfuscate the user profile. A successful download leads to AS2.X. Once the attacker has reached AS2.1, AS2.2, or AS2.3, he or she can execute the malware and exploit the system. Our goal is to be able to make a proper response before the exploit happens.
Defender’s View of the Attack Model. Figure 1b depicts the defender’s view of the same attack model depicted in Figure 1a. Because of the limitations of the monitoring system, the defender has a limited view of the files downloaded in AS2.X. If the malware has a known signature predefined in the monitoring system, the file can be recognized as malware (d2). Otherwise, a malware download will be seen as a benign file download (d3). Such discrepancy in the attack model from the attacker and the defenders perspective supports our claim on the insubstantiality of applying traditional game theoretic models for our security problem.
2. Data Driven Security Models and Analysis
The current security testbed (see Figure 2) consists of a repository of attack containers and an isolated execution environment for the attacks based on Linux Containers. Each attack container contains a complete environment to run the attack and monitoring tools. Included attack artifacts are: executable exploits and vulnerable application-level software. The monitors include network and host monitors, such as Bro or Open Source Host-based Intrusion Detection System (OSSEC), to capture logs of the attack. The logs includes network packet captures (pcap), system and application logs (syslog), and security alerts. The attack containers are implemented as Linux Containers, a lightweight virtualization technique. Containers execute on a host system where isolation between the host and the containers is guaranteed by Linux cgroup. Linux Containers can run major Linux distributions such as Debian or Redhat, allowing us to reproduce a wide spectrum of vulnerabilities such as local privilege escalation or remote exploitation.
We have packaged two high-profile attacks, Heartbleed (CVE-2014-0160) and Shellshock (CVE-2014-6271), so that they can be recreated on our testbed. These attacks were chosen as they can be launch remotely. Moreover, the attacks are technically challenging to study as they involve complex cryptographic protocols and system-level programs. The Bro network security monitor and OSSEC host monitor are installed in the attack containers to collect logs. We plan to release our attack container repository as open-source software to the community.
We aim to build a platform where vendors, organizations, and security researchers can share and reproduce latest attacks for educational and research purpose. While, in this work, we focus only on application-level attacks using Linux Containers, we envision our attack container repository to support lower-level attacks (e.g., kernel-level) or hypervisor-level using Virtual Machines. By providing an execution environment for attacks and comprehensive monitoring infrastructure, our platform allows security researchers to focus on the core features of the attacks, relieving them from low-level technical work of setting up infrastructure.
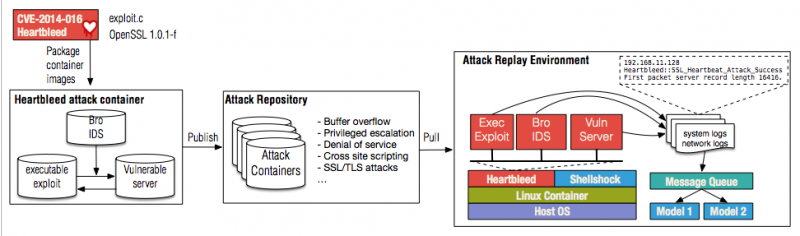
Figure 2: Security testbed: workflow of creating and replaying attack containers


