 Policy Analytics for Cybersecurity of Cyber-Physical Systems: June 2018 (Y1, Q1)
Policy Analytics for Cybersecurity of Cyber-Physical Systems: June 2018 (Y1, Q1)
PI(s), Researchers: Nazli Choucri (Lead)
INTRODUCTION
Mounting concerns about safety and security have resulted in an intricate ecosystem system of guidelines, compliance measures, directives and policy reports for cybersecurity of all critical infrastructure. To date this has resulted in a complex ecosystem of policies that govern usage, data, compliance, cybersecurity directives and other aspects of cyber-physical systems (CPS). By definition, such guidelines and policies are written in linear sequential text form that makes them difficult to integrate, or to understand the policy-technology-security interactions, thus limiting their relevance for science of security. Missing are analytics for smart grid cybersecurity and risk assessment. This project seeks to develop text-to-analytics methods and tools for guidelines on critical infrastructure, with special focus on smart grid technology, a highly complex CPS. Figure 1 highlights the underlying problem.

In addition, several technical barriers impede full understanding of the cyber-physical properties of a smart grid enterprise, for example, (a) locating policy relevant decision points, (b) identifying vulnerabilities embedded in organizational process and technical operations (c) Differentiating intents of threat actor vs. vulnerability of system, (d) tracking damages and diffusion effects, (e) characterizing potential unknown-unknowns, or (e) metricizing functional relationships - to note the most obvious.
HARD PROBLEM(S) ADDRESSED
This work directly addresses the hard problem of policy-governed secure collaboration at the enterprise level (focusing on smart grid in power systems, as a class of cyber-physical systems central to the nation's critical infrastructure). It is especially relevant to the Science of Security program because the design is based on a structured system model derived from critical policy texts designed to (a) identify major system-wide parameters, (b) situate vulnerabilities, (c) map security requirements to security objectives, (d) advance research on how multiple system features interact with multiple security requirements and affect the cybersecurity of critical cyber/physical enterprise, and (e) explore interactions of policy interventions and system-properties, including implications of "drill-down" investigations. Figure 2 defines the project contributions to the set of hard problems.

PUBLICATIONS
Nazli Choucri, Gaurav Agarwal, Xenofon Koutsoukos. 2018. "Policy-Governed Secure Collaboration: Analytics for Cyber-Physical System Cybersecurity." Project Working Paper-1.
KEY HIGHLIGHTS
This quarterly report presents two key highlights of research during this past period. Both are central to the foundations activities. Figure 3 shows a high-level view of the overall research plan to provide the context for the two keys highlights presented below.
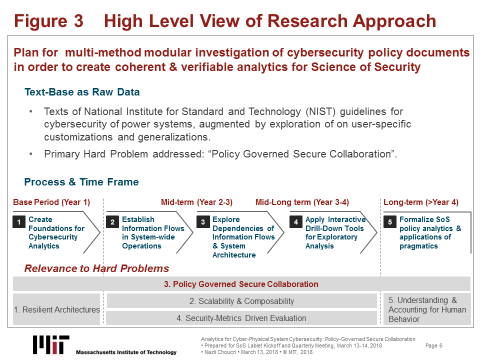
For operational purposes, we focus initially on the cybersecurity of a "generic" or "empirical" smart grid to prepare the tools and process that may be field-tested (pilot study with a potential industry partner, beginning Year 2). Figures 3 provides a high-level summary of the key tasks -- extending in scale and scope tasks as defined in the proposal -- that will be undertaken during this research.
Highlight 1: Definition, Design, and Initiation of Operational Year 1 Plan
The first critical task completed in the first quarter, highlight 1, was articulating the details of the activities for the first year and the foundational tasks for the overall Project. Figure 4 shows the design of the operational plan or Year 1.

As specified in the project proposal, the core data base consists of we focus the "raw text" of policy documents, directives and guidelines - a powerful source of directives based on the extensive research and scientific inquiry from a wide range of institutions, stakeholders, and agencies.
Highlight 2: Defining the Eco-System of Policy Documents
The second highlight derives from the work we have done under items 1 and 2 noted in Figure 3 above - these are defining the policy e-landscape and review of entire e-policy ecology to concentrate on the core. The cyber security of the cyber-physical system examined -- namely critical infrastructure with special focus on smart grid - require attention to two classes of policy documents. Figure 5 shows the key NIST policy documents selected as the core of our CPS investigation. These cover (a) generic directives pertaining to large scale domain independent critical infrastructure and (b) specific documents related to smart grid. Figure 5 also identifies the focal issues addressed in each document.

COMMUNITY ENGAGEMENTS
Our research design and current work was presented at the weekly meeting of the research/consortium on "Cybersecurity at MIT Sloan" focusing on proof-of-concept for the overall design. This is important because we are adopting a multi-method approach that must meet multiple types of critical reviews.
EDUCATIONAL ADVANCES:
The project research design and its implications were included in the curriculum for teaching purposes in the course at entitled Cybersecurity offered jointly by the Department of Political Science and the Sloan School of Management at MIT.


