Policy Analytics for Cybersecurity of Cyber-Physical Systems: January 2019 (Y1, Q3)
Policy Analytics for Cybersecurity of Cyber-Physical Systems: January 2019 (Y1, Q3)
Funding Type: Full proposal
Start Date: March 01, 2018
Expected Completion Date: April 30, 2019
Principal Investigator: Nazli Choucri
Public View
Accomplishments
Accomplishments during this reporting period (Q3) and future activities are presented in the following sections of this Report:
1. Contributions to Science of Security: Policy-Domain
2. Contribution(s) to resolving Hard Problems
3. Progress: Fiscal Year to Date
4. Quarterly Progress - Q3 (October-December 2018).
4.1. Research
4.2. Outreach
5. Publications
6. Planned Activities: January-March 2019
7. References
1. Contributions to Science of Security: Policy-Domain
The overall contribution to the core project was outlined earlier in Q2 Report (July-September 2018) [1]. Here we note only some key points as well as some additional elements. They are all seen in the context of the 2015 White Paper [2] on progress on hard problems that defines the Policy-Governed Secure Collaboration as seeking to:
"... to develop the science underlying methods for expressing and enforcing normative requirements and policies for handling data with differing usage needs and among users in different authority domains."
Recall that the research outputs of this core project include. but are not limited to: (a) methods to examine the implications of cyber security directives and guidelines directly applicable to the system in question, (b) information about relative vulnerability pathways throughout the whole or parts of system-network as delineated by the guidelines documents (c) insights from contingency investigations, that is, "what...if...", (d) framework information management within the organization and (e) ways to facilitate information flows bearing on decision-making for cybersecurity.
In addition, we stress the value of understanding the evolutionary trajectories in policy formulation and development. While in our application case we focus on NIST guidelines - framed in many documents - the relationships among the documents provide signals on the evolution of consensus and, most important of all, on the value of what NIST calls "crosswalks". This enables us to develop cumulative methods for broadening the strategy of "text as data".
Earlier in Report Q2 [1] we also signaled how our work supports the implementation of following normative policy requirements:
- The 2019 National Defense Authorization Act [3],
- The 2017 Presidential Executive Orders on "Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure" (EO 13800) [4], and
- The 2018 US Department of Defense Cyber Strategy [5].
There is no need to repeat this discussion, however, it is useful to note again that the newly released DoD Cyber Strategy [5] is based on four pillars. Our current work contributes to Pillar 2: "Compete and Deter in Cyberspace" requires to "increase the resilience of U.S. critical infrastructure":
"...The Department will work with its interagency and private sector partners to reduce the risk that malicious cyber activity targeting U.S. critical infrastructure could have catastrophic or cascading consequences. We will streamline our public-private information-sharing mechanisms and strengthen the resilience and cybersecurity of critical infrastructure networks and systems." [5, p5] [Bold added by author].
The current work concentrates on the operational manifestations of the conceptual elements of smart grid at a generic. Nonetheless, it enables data pursuit of views and analyses from alternative perspectives, thus increasing the value of the work and expands the available information content.
In addition to the contributions noted in Q3 Report (July-Sept. 2018) [1] we have identified an important addition bearing on cyber security from operational and mission, namely institutional mechanisms that impede cyber effectiveness in the military. Specifically, in conjunction with collaborators from USAF we explored the operational policy-related constraint and challenges that US Air Force faces in acquisition of cyber assets essential for maintaining US air superiority. These are further analyzed in context of Section 1635 on Defense Acquisition [6] of 2019 NDAA [3] (See [7] for complete paper and [8] for a related article).
2. Contribution(s) to resolving Hard Problems
By definition, "Hard Problems" are elusive because: (i) the problem properties are not readily processed by traditional or well recognized modes of inquiry; (ii) the issue area or domain has not been subject to extensive analysis to date; (iii) the underlying dynamics reflect a daunting complexity, (iv) data-creation is a necessary but not sufficient condition for progress; and (iv) system boundary may not be readily defined; and (iv) temporality may take on many forms--to note only some of the most daunting elements. Our major contribution to the specific hard problem we address is dealing with "text-as-data" in a complex cyber-physical where threats to operations serve as driving motivations for policy responses.
3. Progress: Fiscal Year to Date
As outlined in the project proposal, this core project develops a multi-method modular approach applied to a generic system in a controlled environment. The application case focuses on policy supporting cybersecurity of smart grid in electric power systems. The tasks in Year 1 are to: identify the relevant policy ecosystem, formalize rules to extract data from text, and design an internally consistent framework and structure to organize, metricize, and manage critical data in the application domain.
The application case focuses on texts of policy and guidelines issued National Institute for Standard and Technology (NIST) for cybersecurity of power systems. These texts constitute the "raw data" for our investigations. Figure 1 presents the near-, mid- and long- term project goals, centered on "Policy Governed Secure Collaboration" as the primary hard problem.

Figure 1. Near-, mid- and long- term project goals
The tasks in Year 1 establish foundations for analytics of cybersecurity for cyber-physical systems and demonstrate the implementation for the application case. Table 1 summarizes the scope of work and overall progress made till date. In the course of this work we have streamlined the tasks to reduce potential digression from core goals. Table 1 below provides a status-report, task by task, and progress therein.
Table 1 Task 1 (Year 1) Progress to date
Scope of work and progress made in (March-December 2018)

Note: Previous version presented in earlier Quarterly Report
4. Quarterly Progress - Q3 (October-December 2018)
Q3 Progress is summarized below with respect to research, outreach, and development / administrative issues.
4.1. Research
MIT Team continued work as planned on the data extraction. In addition, the team is preparing for year 2 on construction of design structure matrices as structured model of the overall application system. We are also developing tools for customized analysis to meet the need of different constituencies beyond the application case for this project.
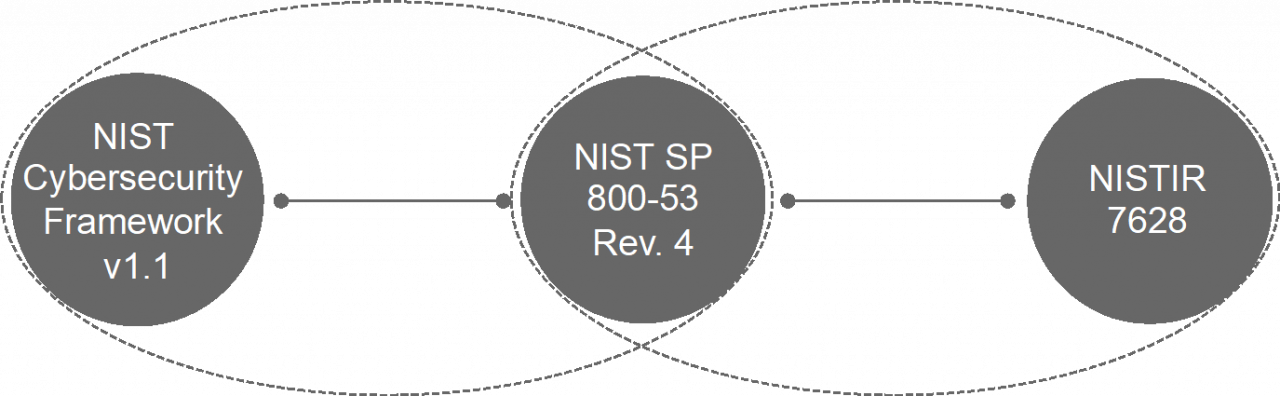
Concurrently, we have developed a view of the overall policy ecosystem within which we can situate the policy texts that to use as "raw data". In Figure 2 we situate the NIST initiatives on smart grid cybersecurity within a broader policy ecosystem.

Figure 2. NIST Cybersecurity Ecosystem
Clearly policy positions evolve over time. Their evolution represents a consolidation of posture and position. Figure 3 presents some highlights in the evolution of NIST guidelines and directives. This evolution is also an evolution of the focus of the entity itself.
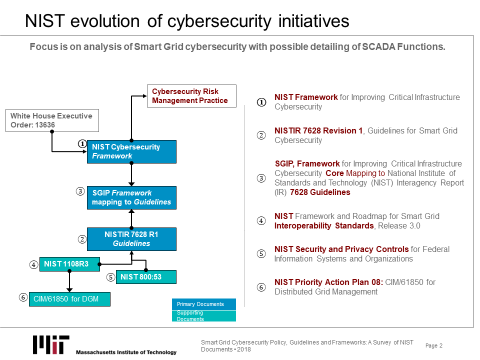
Figure 3. Evolution of NIST Cybersecurity Initiatives
Continuing work conducted in Q2 (June-September), the team focused on extraction of data from the source of our texts if "raw-data". We selected the cumulative materials in the NISTIR-7628 on Guidelines for Smart Grid Cybersecurity [2] as well as the NIST Cybersecurity Framework (CSF) [3]-- all totaling more than 600 pages. Especially relevant is that these two data-texts are connected other via a third policy text namely, NIST SP 800:53 Rev.4 [4] on Security and Privacy Controls for Federal Information Systems and Organizations, shown in Figure 4.
Given the application case, we focused on NISTIR-7628 Guidelines as the text-based raw data, and then augment our investigations with the Framework. the text-content lineage of NISTIR 7628 carries fundamental knowledge and provides detailed information on this NIST conceptual representation of smart grid, its actors and activities; the interfaces between actors and their attributes as well as notional views of relationships. A simplified schematic view is shown in Figure 2 below. The challenge is to operationalize the links and rendering them in digital terms for a structural model.
|
|
|
Figure 4. Connections of NIST 7628 and NIST CSF. (shown earlier in Quaterly Report 3.) |
Given the application case, we focused on NISTIR-7628 Guidelines as the text-based raw data, and then augment our investigations with the Framework. the text-content lineage of NISTIR 7628 carries fundamental knowledge and provides detailed information on this NIST conceptual representation of smart grid, its actors and activities; the interfaces between actors and their attributes as well as notional views of relationships.
Figures 2, 3 and 4 help contextualize the application case in a broader policy context. Figure 5 below highlights the role of NIST in the specific domain of smart grid cybersecurity.

Figure 5. The Application Case
In Quarterly Report 2 we presented an early schema of the proposed process for creating a structured model from the policy directives of the application case (Figure 4 above). In Figure 6 we show the value to an enterprise (business and industry) anchored in the NIST Cyber Security Framework (right side of Figure 4).

Figure 6. Expected Value of Cyber Risk Managment
At this point most of the "pieces" are in place, and we are now able to complete last tasks planned for year 1 (see Table 1 above)
4.2. Outreach
Here we differentiate among different forms of outreach.
-
Collaboration with Military: MIT-PI is collaborating with USAF on dilemmas of rapid acquisition and cyber-specific challenges. Current discussion and assessments lead to an understanding that current rapid acquisition does not automatically equate to fielded capabilities. The struggle revolves around "developmental and operational test" of capabilities prior to fielding. Today's waterfall acquisition models employ developmental test milestones throughout the development cycles, then push to operational testing before fielding. USAF recognizes the need to move toward more agile acquisition mechanisms - at least for software development, where these tests are integrated throughout the development process (with as much automation as possible) vice independent milestones along the way. A joint paper highlighting the challenges and potential strategies for moving forward has been presented at the 2018 CyCon [9] for post conference publication. We are in discussion with 318th Cyberspace Operations Group, 688th Cyberspace Wing, Joint Base San Antonio-Lackland Texas [10] for potential collaboration in this field.
-
Panel on Future of Cybersecurity. The MIT- PI shared a panel with Major General Yee [11], U.S. Army Director of Cybersecurity and Information Assurance on the sidelines of the New World Powers: Global Security Forum, and Maj. Gen. (ret) Michael Jones, Former Chief of Staff of U.S. Central Command (USCENTCOM) at a. meeting organized by The World Affairs Council of CT at Hartford, CT on Bytes and Bullets: The Future of Cybersecurity (October 19 - October 20, 2018). See event information: https://www.ctwac.org/event/global-security-forum-new-world-powers. This panel provided an opportunity to introduce the SoS program to the audience and share its various aspects with Major General Yee and Major General (ret) Jones.
-
Education: MIT-PI completed the graduate-level class on International Relations Theory in the Cyber Age. Four US DoD military officers, currently MIT, successfully completed the course work. We are now exploring on how to develop and sustain an interest in SoS and other potential DoD policy relevant projects.
-
SoS Events: MIT PI participated in a quarterly SoS meeting [12] held on-campus at Carnegie Mellon University on October 29-30, 2018.
-
Collaboration with Academia and Industry: The validation study of "text-as-data" on cyber operations during war (Tallinn Manual 2.0 [13]) -- we have conducted earlier as proof of concept for the research methodology -- is now been prepared for circulation and publication.
5. Publications
-
Klemas, Thomas, Rebecca K. Lively and Nazli Choucri. 2018. "Cyber Acquisition: Policy Changes to Drive Innovation in Response to Accelerating Threats in Cyberspace." 2018 International Conference on Cyber Conflict U.S. (CyCon U.S.), November 14-15, 2018, Washington DC. https://cyberdefensereview.army.mil/Portals/6/Documents/CyConUS18%20Conference%20Papers/Session2-Paper3.pdf?ver=2018-11-13-160900-057
-
Choucri, Nazli and Gaurav Agarwal. 2018 "International Law for Cyber Operations: Complexity and Transparency" in preparation.
6. Planned Activities: January-March 2019
The work for January-March will focus on completing Task 1 (all items in Year 1 plan), and reporting on results framed by the scope of work summarized Table 1 above.
- https://cps-vo.org/node/56209
- Nicol, D., B. Sanders, J. Katz, B. Scherlis, T. Dumitras, L. Williams, and M.P. Singh. 2015. Science of Security lablet: Progress on Hard Problems. p2. https://cps-vo.org/node/21590
- https://www.congress.gov/bill/115th-congress/house-bill/5515/text
- https://www.whitehouse.gov/the-press-office/2017/05/11/presidential-executive-order-strengthening-cybersecurity-federal
- Department of Defense. 2018. Cyber strategy. https://media.defense.gov/2018/Sep/18/2002041658/-1/-1/1/CYBER_STRATEGY_SUMMARY_FINAL.PDF
- https://www.congress.gov/bill/115th-congress/house-bill/5515/text#toc-H7A1F000DE6B544A0884F9E612B08E3BF
- https://cyberdefensereview.army.mil/Portals/6/Documents/CyConUS18%20Conference%20Papers/Session2-Paper3.pdf?ver=2018-11-13-160900-057
- https://www.fifthdomain.com/dod/2018/11/26/why-cyber-compounds-pentagon-purchasing-problems/
- http://aci.cvent.com/events/2018-international-conference-on-cyber-conflict-cycon-u-s-/event-summary-e48766aa586c4bf2900503339dbbab66.aspx?dvce=1
- https://www.afcyber.af.mil/About-Us/Fact-Sheets/Display/Article/962022/318th-cyberspace-operations-group/
- https://cdn.ymaws.com/www.alamoace.org/resource/resmgr/2017_ace/2017_speakers/doc_yee_garrett2017.pdf
- https://cps-vo.org/node/57210
- https://www.cambridge.org/core/books/tallinn-manual-20-on-the-international-law-applicable-to-cyber-operations/E4FFD83EA790D7C4C3C28FC9CA2FB6C9