Policy Analytics for Cybersecurity of Cyber-Physical Systems: April 2019 (Y1, Q4)
Policy Analytics for Cybersecurity of Cyber-Physical Systems: April 2019 (Y1, Q4)
Funding Type: Full proposal
Start Date: March 01, 2018
Expected Completion Date: April 30, 2019
Principal Investigator: Nazli Choucri
Public View
Accomplishments
Accomplishments during this reporting period (2019-Q4) and Planned Activities for year 2 are presented in the following sections of this Report:
1. Contributions to Science of Security: Policy-Domain
1.1 Contribution(s) to Addressing Hard Problems
1.2 Year 1 Activities
1.3 Past Progress: April - December 2018
2. Current Progress: January - March 2019
3. Text as Raw - System Structure & Process
4. Rules for Extracing Data form Text
5. Plan Developed for Year 2
6. Administrative
7. Education
8. References
1. Contributions to Science of Security: Policy-Domain
The first quarterly report for year 1 [1] outlines the purpose of the project as a whole -over and above the proposal statement. Specific contribution to made to the core project are outlined in the second quarterly report [2] and in third quarterly report [3]. Additionally, the research contributes to the 2019 National Intelligence Strategy of United States of America [4], specifically the topical mission objective 4 on Cyber Threat Intelligence:
"Detect and understand cyber threats from state and non-state actors engaged in malicious cyber activity to inform and enable national security decision making, cybersecurity, and the full range of response activities."
Our project focusing on cyber-physical system for cybersecurity of electrical smart grids - as an example of critical infrastructure - works tol provide an opportunity for "under the hood" understanding of policies and directives to provide incentives for greater than "compliance only" reponses, and greater understanding of systems relationships and interdependencies.
1.1 Contribution(s) to Addressing Hard Problems
This project on the "policy governed secure collaboration" is for managing cybersecurity risk by capturing the full-value of sector or critical infrastructure specific cybersecurity guidelines. As outlined in the project proposal, the research consist of a multi-method modular approach applied to a generic infrastructure system in a controlled environment. The "raw data" consists of texts of National Institute for Standard and Technology (NIST) guidelines, policies and directives for cybersecurity of power systems, augmented by exploration for user-specific customizations and generalizations.
For context, Figure 1 provides once more the near-, mid- and long- term project goals, with "Policy Governed Secure Collaboration" as the primary hard problem.
|
|
|
Figure 1. Near-, mid- and long- term project goals Source: Analytics for Cyber-Physical System Cybersecurity: January 2019 [1]. |
1.2 Year 1 Activities
Task 1 in Year 1 focuses on creating foundations for cybersecurity analytics. Table 1 summarizes the scope of work and signals the overall progress targeted.
|
Table 1. Task 1 (Year 1) Scope of work and progress made in Year 1 |
|
|
While the items in Table 1 are presented sequentially, the actual research cannot and does not follow this discrete listing.
1.3 Past Progress: April - December 2018
Progress made between April - December 2018 are available here:
- Analytics for Cyber-Physical System Cybersecurity: January 2019 [1]
- Analytics for Cyber-Physical System Cybersecurity: October 2018 [2]
- Analytics for Cyber-Physical System Cybersecurity: July 2018 [3]
The following sections of this report summarize the progress in the remaining three months of the Year 1 effort: January - March 2019.
2. Current Progress: January - March 2019
In this quarter, the work resulted in completing of three critical tasks:
1. Constructing Text-as-Raw Data"
- Conceptual model of NIST for smart grid NISTIR-7628 on Guidelines for Smart Grid Cybersecurity
- Cumulative materials provided in other NIST sources and cumulating in the NISTIR-7628
- Customized data for this application from NIST Cybersecurity Framework.
2. Designing Rules for Extracting Data from Text
3. Developing Plan for Year 2
The sections below detail the work on each component
3. Text as Raw Data - System Structure & Process
At this point we highlight our approach to generate "raw-data" and our uses of these to build the data set for metricization. We begin with NIST Conceptual Model. Our purpose at this point is to provide a more user-friendly or operational approach to the contents of. We do so by organizing the overall system structure and process into to yield a coherent framework of the system" as is", as well as its fundamental vulnerabilities and security objectives.
Table 3 Summary of Characateristic Features of Raw Data Base
_______________________________________________________________________________
The Raw Data Base is:
Anchored in
"As Is State" of Infrastructure Specific System
-
Actor and domain (or function)
-
Logical interfaces
Augmented by:
Vulnerabilities, Security Objectives, Impacts, Requirements
-
Vulnerabilities for each of actors and domains
-
Security objectives
-
Impact for each of the three-security objectives of system:
availability, information integrity and customer confidentiality
-
applicable Security requirements
Augmented by
Customized application of Cybersecurity Framework to "As Is State"
-
applicable sub-categories, categories and functions of NIST Cybersecurity Framework.
_______________________________________________________________________________
This now completes the task of identifying the bguildling blocs and building a raw data base from text. The process yields a cumulative "onion like" data base.
4. Rules for Extracting Data from Text
The data-extraction strategy undertaken after developing a design for the raw data is shown in Figure 4. This figure provides a high-level view of the vastness of the information embedded in NISTIR-7628 (and its supporting texts). It is designed to show the linkage-strategy to connect the components of policy-governed security for cyber-physical systems.
|
|
|
Figure 4. The overall linkage strategy |
A more detailed discussion of the overall system - in parsed form - is prepared to be provided in the first Quarterly Report of Year 2
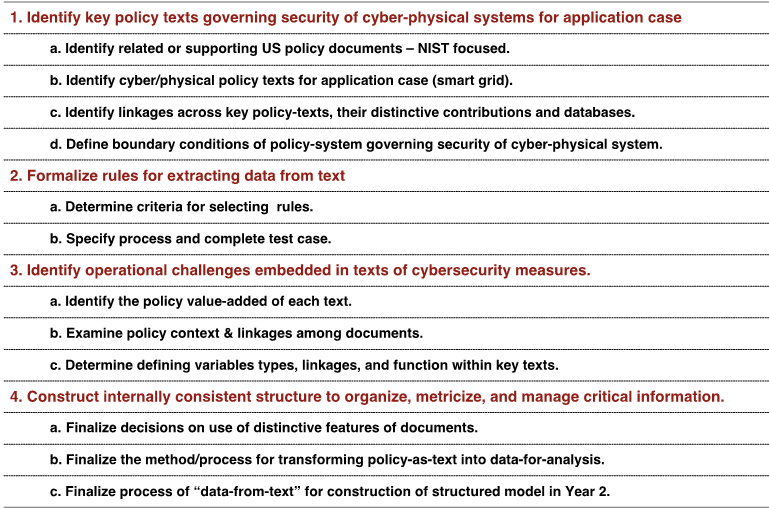
5. Plan Developed for Year 2
Building on the Year 1 results, in Year 2 we will focus on Task 2 to "Establish Information Flows in System-wide Operations" (see Figure 4). By following the linkage strategy in Figure 4 w e can then create dependency structure matrix (DSM) of Smart Grid Cyber-Physical System in metricized form. This is done by (i) following the structure in Table 3, (ii) identifying first level information dependencies; and (iii) cluster and partition DSM to reveal "hidden features". The table below shows tentative plan for year 2.
|
Table 4. Planning for Year 2 Tasks. |
|
|
6. Administrative:
Continuing on the white paper for "Security of Global Undersea Networks: Models, Defenses, and Policy Mechanisms" in response to current Agency hard question Long-Chain Analysis of Dynamic and Mobile Infrastructure that Lablet members could help address, MIT-PI is completing a case study on China.
7. Education:
MIT-PI is teaching a graduate-level class on International Relations Theory in the Cyber Age, drawing on policy-relevant materials. The course draws from student participants from different parts of MIT. 2015 edition of the course is now available at: https://ocw.mit.edu/courses/political-science/17-445-international-relations-theory-in-the-cyber-age-fall-2015/
8. References
- https://cps-vo.org/node/57492
- https://cps-vo.org/node/56209
- https://cps-vo.org/node/54641
- https://media.defense.gov/2018/Sep/18/2002041658/-1/-1/1/CYBER_STRATEGY_SUMMARY_FINAL.PDF
- Nazli CHouci and Guarav Agarwal, Report for Year 1, 2019