Policy Analytics for Cybersecurity of Cyber-Physical Systems: July 2019 (Y2, Q1)
Policy Analytics for Cybersecurity of Cyber-Physical Systems: July 2019 (Y2, Q1)
Funding Type: Full proposal
Start Date: March 01, 2018
Expected Completion Date: April 30, 2020
Principal Investigator: Nazli Choucri
Public View
Accomplishments
Accomplishments during this reporting period: April 2019 - June 2019 (Year 2: Quarter 1) are presented in the following sections of this report. By necessity, reference to Year 1 is made.
Table of Contents
1. Problem Statement
1.1 Purpose
1.2 Focus
2. Project Anchors: Support to National Cyber Security Strategy and Policy
3. Aligning Project Vision and Mission to National Cybersecurity Policy (Accomplishment 1)
4. Review of Research Design: Platform for Cybersecurity Analytics
5. Identifying the Policy-Relevant Ecosystem (Accomplishment 2)
6. Design of Data Extraction and Linkage Method (Accomplishment 3)
7. Pre-Testing the Operational Framework (Accomplishment 4)
8. Technical Challenges
9. Publications
10. Contributions to SoS Program
11. New Directions
12. References
1. Problem Statement
As a general practice, guidelines, directives and policy documents are presented in text form, page-by-page and word-by-word - supported with figures, diagrams and tables as needed. Rooted in the legal tradition, this practice reinforces a linear logic, where sequence dominates, and the focus is on compliance, step-by-step. Invariably this situation supports a checklist approach to meeting requirements.
By definition, text undermines any attention to feedback, delays, interconnections, cascading effects, indirect impacts and the like - all embedded deep into the idiom or structure of the textual form. Figure 1 highlights the opportunity costs of cybersecurity guidelines.
|
|
|
Figure 1. The Underlying Problem |
The text-form may be necessary, but it is not sufficient. In fact, it may create barriers to understanding, obscure the full nature of directives, and generate less than optimal results - all of which impede the pursuit of effective outcomes.
1.1 Purpose
The overarching purpose of this project is to support national strategy for cybersecurity, as outlined in Presidential Executive Orders (EXORD) and National Defense Authorization Acts (NDAAs). Operationally, our goal is to develop analytics for cyber security policies and guidelines targeted specifically to (a) generate correctives for the policy features in Figure 1, (b) extract the knowledge embedded in policy guidelines, and (c) assist the user community, analysts, and operators in implementation.
The Cyber Security Framework (CSF) is mandatory in the public sector, and greatly encouraged for the private sector. CSF provides general guidance and directives of a broadly defined nature. But the mission -specific application is left to the user - with only the general guidance provided in CSF. It is up to the user to proceed as best determined.
We situate this research project at the interface of users and CSF, in order to facilitate access to, and use, of CSF. The general purpose here is to help users and, in the process, provide tools to explore mission-related properties, concerns, or contingencies. For this reason, we have designed the entire project in modular terms, based on a structured model of system properties. Different users may prefer to use different features and/or draw on results (or products) generated at different phases of this project, as noted below.
1.2 Focus
Focusing on the salience of cybersecurity in both private and public sectors, we draw on major reports presented by the National Institute for Standards and Technology (NIST) as the source of our data. This material is rich in content, based on considerable background and collective knowledge, and subjected to a careful scrutiny and evaluation.
While some efforts [1, 2, 3 and 4] have already been made to mine NIST materials, few exploit [5, 6, 7 and 8] the value of multi-methods for knowledge mining and analytical tools to support user understanding, analysis, and eventually action. References [5-6] visualize the information on smart grid conceptual model provided in reference [9]. Reference [7] examines the relationships or dependencies within the same conceptual model and then restructures it. Reference [8] provides a filtered view of the conceptual model for electric vehicle.
Detailed further below, our approach learns from, and transcends, the above by developing a platform for multi-methods cybersecurity analytics based entirely on the contents of policy documents. The case application focuses on cybersecurity of smart grid for electric power systems. The smart grid is a ubiquitous CPS, central to all critical infrastructures. And we use notable NIST reports on smart grid cybersecurity as well as on reports on cybersecurity for other sectors.
The application case uses only policy documents as its database. As such, it is in a "controlled environment". Further, the structured model (for any application) includes operational linkages to NIST-CSF to be set for mission-specific security requirements.
2. Project Anchors: Support to national Cyber Security Strategy Policy
This project is guided by two sets of policy anchors that define national priorities for cybersecurity of critical infrastructure. First are Presidential Executive Orders (EXORD). Figure 2 below we show segments of EXORD issued in 2019 [10] and 2017 [11]
|
|
|
Figure 2. Presidential executive orders on securing information and Communications Technology |
The second policy anchors are NDAA for 2019 [12] and for 2018 [13]. Figure 3 shows segments of each.
|
|
|
Figure 3. NDAA on protection of critical infrastructure |
3. Aligning Project Vision and Mission to National Cybersecurity Policy (Accomplishment 1)
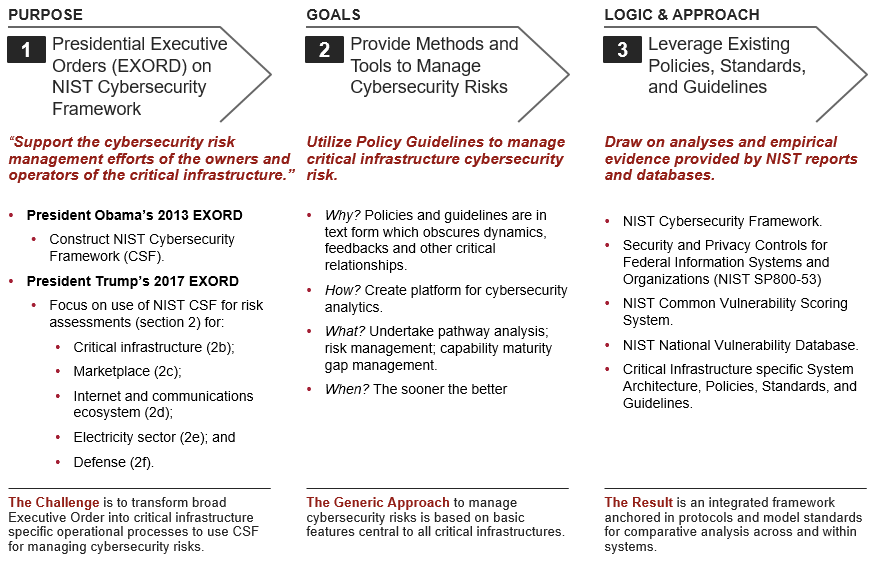
Our first accomplishment in Year 1 is aligning our project with national policy by consolidating our vision and mission around EXORD and NDAA statements in Figure 2 and 3 above. This alignment ensures that our research project remains anchored in national policy priorities. Below we show high level views of both vision and mission This is necessary in order to not lose sight of the "big picture" when we "delve into details" later on.
In Figures 4 we provide a detailed accounting of our orientation (steps 1-3) with respect to purpose, goals, and logic and approach. Figure 5 can be seen as continuation of Figure 4, but it focuses on operational imperatives.
|
|
|
Figure 4. Support for national cybersecurity policies - vision and mission |
|
|
|
Figure 5. Support for national cybersecurity policies - activites and outcomes |
4. Review of Research Design: Platform for Cybersecurity Analytics
The vision and mission in Figures 4 and 5 above are entirely consistent with the initial research design put forth in the project proposal. Figure 6 below shows the initial research design by way of placing Year 1 in context, as well as Year 2 which depends on the products of Year 1.
|
|
|
Figure 6. Project research design |
The remainder of this Quarterly report is devoted to accomplishments in Year 1 as they bear directly on Year 2, and on accomplishments in Year 2 Quarter 1.
5. Identifying the Policy-Relevant Ecosystem (Accomplishment 2)
Figure 7 shows our reconstruction of the cybersecurity timeline. It highlights the policy ecosystem and serves as the larger frame of reference for the subsequent accomplishments reported here.
|
|
| Figure 7. Cybersecurity policy development - timeline of policy ecosystem |
|
|
In Figure 8 we show the specific policy documents that are used for cyber analytics of smart grid, the application case. These are directives whose texts constitute our baseline for metricization. The figure differentiates between those focused on NIST-cybersecurity for smart grid and those addressing challenges to cybersecurity of critical infrastructures more broadly defined.
|
Figure 8. Core policy documents for "Text-to-Data" |
6. Design of Data Extraction and Linkage Method (Accomplishment 3)
The two first accomplishments are presented here as a part of Year 1. Year 2 and all subsequent research-years depend on the products of Year 1, we consider these as foundational.
7. Pre-Testing the Operational Framework (Accomplishment 4)
We undertook a pre-test on an independent "text-to-data" extracted from the Tallinn Manual 2.0 on the International Law Applicable to Cyber Operations [23] to validate the method, and verify internal consistency of data extraction & linkages to support metrics and generate output of process from policy texts to text-as-data.
This pre-test is on a "simple case" one less complex than the combination of NIST documents we use. Nonetheless, it helped to identify steps to avoid for operational efficiency, and provided an opportunity to explore the automation of data extraction and transformation. Results of the pre-study are in "International Law for Cyber Operations: Networks, Complexity, Transparency" [25].
8. Technical Challenges
Framed in the context of accomplishments for Year 1 and for year 2 Q1, we here identify a major challenge, and there could be more. All steps in the construction of the structured model - the DSM - were done "by hand" and hence very time consuming. Several rounds were done to make sure that human errors would be identified. Clearly this calls for automation. But we had not anticipated that challenge in our research proposal and budget.
9. Publications
- MIT-PI completed the paper on "International Law for Cyber Operations: Networks, Complexity, Transparency" [25]. This paper is a "test" for the approach and logic developed in Year 1 based on Tallinn Manual 2.0 on the International Law Applicable to Cyber Operations [23].
- In response to upcoming hard problem on securing long-chain of a global mobile infrastructure, a study was undertaken on how actors in the international system share the global cyber-physical system of undersea communication cables. A White Paper on "Imperatives for Securing the Long-Chain of Cyber-Physical Global Communication Infrastructure" [24] was submitted to SoS, and to upcoming IEEE Symposium on Technologies for Homeland Security.
10. Contributions to SoS Program
Figure 10 provides ta summary of contributions to the SoS program:
|
|
|
Figure 10. Contributions to SoS Program |
11. New Directions
MIT-PI is exploring options to use edX platform for training future DoD manpower on cybersecurity education. This topic has been discussed in 2019 NDAA [13] as well as in Presidential Executive Order 13870 on America's Cybersecurity Workforce [29]. This topic is not yet addressed in this current SoS Project.
12. References
- Cyber Security Procurement Requirements Traceability for the Electric Sector, Electric Power Research Institute, Palo Alto, CA, Tech. Rep. 3002003331, 2014. https://www.epri.com/#/pages/product/3002003255/
- Security Posture using the Electricity Subsector Cybersecurity Capability Maturity Model (ES-C2M2), Electric Power Research Institute, Palo Alto, CA, Tech. Rep. 3002003332, 2014. https://www.epri.com/#/pages/product/3002003332/
- Risk Management in Practice, Electric Power Research Institute, Palo Alto, CA, Tech. Rep. 3002003333, 2014. https://www.epri.com/#/pages/product/3002003333/
- Cyber Security Risk Management in Practice, Electric Power Research Institute, Palo Alto, CA, Tech. Rep. 3002004712, 2014. https://www.epri.com/#/pages/product/3002004712/
- M. Harvey, D. Long and K. Reinhard, "Visualizing NISTIR 7628, Guidelines for Smart Grid Cyber Security," 2014 Power and Energy Conference at Illinois (PECI), Champaign, IL, 2014, pp. 1-8. https://ieeexplore.ieee.org/document/6804566
- D. Long, B. Drennan, and K. Reinhard, "NISTIR 7628 Visualization", Cyber Resilient Energy Delivery Consortium (cred-c.org). https://cred-c.org/sites/default/files/posters/19_SynchDataQ_Poster_CREDC%20IW%2017.pdf
- B. Rogers and E. Gilbert, "Identifying architectural modularity in the smart grid: an application of design structure matrix methodology", Grid-Interop Forum, Phoenix AZ, 2011. https://sdm.mit.edu/news/news_articles/webinar_082012/rogers_082012.pdf
- A. C. F. Chan and J. Zhou, "On smart grid cybersecurity standardization: Issues of designing with NISTIR 7628," in IEEE Communications Magazine, vol. 51, no. 1, pp. 58-65, January 2013. https://ieeexplore.ieee.org/document/6400439
- NIST, "Guidelines for Smart Grid Cybersecurity," NISTIR 7628, Revision 1. September 2014. https://doi.org/10.6028/NIST.IR.7628r1
- Trump, D., "Executive Order 13800: Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure," Federal Register, 82 FR 22391, pp. 22391-22397. May 11, 2017. https://www.federalregister.gov/d/2017-10004
- Trump, D., "Executive Order 13873: Securing the Information and Communications Technology and Services Supply Chain," Federal Register, 84 FR 22689, pp. 22689-22692. May 15, 2019. https://www.federalregister.gov/d/2019-10538
- H.R.2810 - National Defense Authorization Act for Fiscal Year 2018. Public Law No: 115-91, December 12, 2017. https://www.congress.gov/bill/115th-congress/house-bill/2810
- H.R.5515 - John S. McCain National Defense Authorization Act for Fiscal Year 2019. Public Law No: 115-232, August 13, 2018. https://www.congress.gov/bill/115th-congress/house-bill/5515/text
- NIST, "Framework for Improving Critical Infrastructure Cybersecurity," version 1.1. April 16, 2018. https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf
- NIST, "Guide for Applying the Risk Management Framework to Federal Information Systems," NIST Special Publication 800-37, Revision 2. December 2018. https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-37r2.pdf
- NIST, "Security and Privacy Controls for Federal Information Systems and Organizations," NIST Special Publication 800-53, Revision 4. April 2013. https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r4.pdf
- NIST, "Guidelines for Smart Grid Cybersecurity," NISTIR 7628, Revision 1. September 2014. https://doi.org/10.6028/NIST.IR.7628r1
- NIST, "NIST Framework and Roadmap for Smart Grid Interoperability Standards, Release 3.0," IST Special Publication 1108r3. September 2014. http://dx.doi.org/10.6028/NIST.SP.1108r3.
- NERC," CIP Standards." https://www.nerc.com/pa/Stand/pages/cipstandards.aspx
- NIST, "National Vulnerability Database." https://nvd.nist.gov
- Department of Energy, "Cybersecurity Capability Maturity Model (C2M2)." https://www.energy.gov/ceser/activities/cybersecurity-critical-energy-infrastructure/energy-sector-cybersecurity-0-0
- FIRST, "Common Vulnerability Scoring System." https://www.first.org/cvss/
- Schmitt, Michael N. 2018. Tallinn Manual 2.0 on the International Law Applicable to Cyber Operations. 2017. New York: Cambridge University. https://ccdcoe.org/research/tallinn-manual/
- Choucri, N. and Agarwal, G., "Imperatives for Securing the Long-Chain of Cyber-Physical Global Communication Infrastructure," in publication.
- Choucri, N. and Agarwal, G., "International Law for Cyber Operations: Networks, Complexity, Transparency (December 1, 2018). MIT Political Science Department Research Paper No. 2018-24. https://ssrn.com/abstract=3335183
- Steward D. V., "On an Approach to Techniques for the Analysis of the Structure of Large Systems of Equations," SIAM Review 4 (4):321-342, 1962. https://epubs.siam.org/doi/pdf/10.1137/1004088
- Browning T. R., "Design Structure Matrix Extensions and Innovations: A Survey and New Opportunities," in IEEE Transactions on Engineering Management, vol. 63, no. 1, pp. 27-52, Feb. 2016. https://ieeexplore.ieee.org/document/7332930
- Browning T. R., "Applying the design structure matrix to system decomposition and integration problems: a review and new directions," in IEEE Transactions on Engineering Management, vol. 48, no. 3, pp. 292-306, Aug 2001. https://ieeexplore.ieee.org/document/946528
- Trump, D., "Executive Order 13870: America's Cybersecurity Workforce," Federal Register, 84 FR 20523, pp. 20523-20527. May 2, 2019. https://www.federalregister.gov/d/2019-09750