 Multi-model Testbed for the Simulation-based Evaluation of Resilience (January '20)
Multi-model Testbed for the Simulation-based Evaluation of Resilience (January '20)
PI(s), Co-PI(s), Researchers:
- Peter Volgyesi (PI)
- Himanshu Neema (Co-PI)
HARD PROBLEM(S) ADDRESSED
This refers to Hard Problems, released in November 2012.
- Security Metrics Driven Evaluation, Design, Development, and Deployment
- Resilient Architectures
The goal of the Multi-model Testbed is to provide a collaborative design tool for evaluating various cyber-attack / defense strategies and their effects on the physical infrastructure. The web-based, cloud-hosted environment integrates state-of-the-art simulation engines for the different CPS domains and presents interesting research challenges as ready to use scenarios. Input data, model parameters, and simulation results are archived, versioned with a strong emphasis on repeatability and provenance.
PUBLICATIONS
None.
KEY HIGHLIGHTS
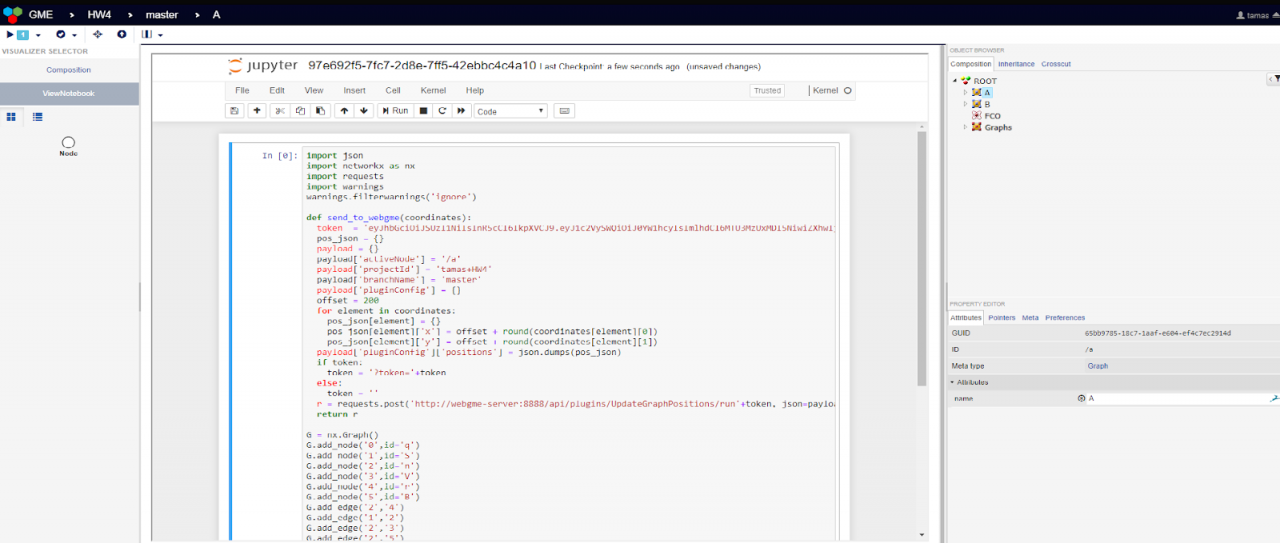
In this reporting period, we circled back and followed through with one of our previous goals to provide a richer developer/analysis environment within the testbed. Since the Fall of 2017, we have been working on a Jupyter Notebook integration capability in WebGME, which would allow Python-based data exploration and/or model modifications to be implemented. By the end of last year, we managed to deliver the first working prototype of this feature (see Figure below).
The current notebook-based workflow and the key architectural elements are as follows:
- A (Javascript-based) WebGME plugin can programmatically generate Jupyter Notebooks, based on the contents of the model. Note, that this plugin can translate the visual (WebGME) model to an arbitrary Python data structure (e.g. NetworkX graph). Alternatively, the Python code inside the Notebook can access the WebGME server via its REST API to query elements of the model.
- The Jupyter Notebook server (co-hosted with the WebGME server) is accessed with a simple iFrame-based visualizer inside the WebGME interface
- With generated notebook code developers can implement custom analysis algorithms and may send data back to WebGME (modify the model)
- The model modification is supported by another (Javascript-based) plugin that has direct access to the model
FUTURE PLANS
During the reporting period, we put our DeepForge / GridLAB-D integration efforts on hold. In its current form, both extension toolsets are hosted in the same WebGME server instance. However, the models (and metamodels) are kept separately in the Model Database and we rely on lightweight cross-project links between DeepForge ML models and GridLAB-D simulation models.
We plan to demonstrate an end-to-end integrated workflow between DeepForge and GridLAB-D in Spring 2020, using one of the previously developed Load Forecasting models. The goal is to automatically invoke the power grid simulation step and collects its results in the DeepForge pipeline.
Similarly, the modernization of the HLA simulation integration toolset remained a planned effort. One of the weaknesses of the current testbed is the missing COA feature set to inject cyber-attacks based on time and event triggers. This is due to the current lightweight integration architecture with direct drivers towards the domain-specific simulation tools. This decision was in part influenced by the fact that the original C2WT integration framework became outdated.
There is a renewed effort to modernize the HLA-based simulation integration toolset, by (1) updating to Portico 2.2.0, (2) enabling support for the new/updated services developed in HLA-Evolved, (3) supporting specification, configuration, and execution of scalable federations by utilizing the hierarchical composition functionality in the centralized RTI architecture (4) supporting the specification, configuration, and execution of message filters that
restrict information flows only to intended recipients and thus provide security. We plan to leverage this effort and use the updated platform in our testbed. One (most) important immediate benefit will be the renewed capability of simulating communication network effects.
COMMUNITY ENGAGEMENTS, TECHNOLOGY TRANSFER
We visited the Cybersecurity Research Group at Fujitsu System Integration Laboratories Ltd. in Tokyo, Japan between November 24-27, 2019. During this visit, we made technical demonstrations of the WebGME/DeepForge platform and discussed our results and experiences with the development of the Lablet testbed. We also presented the Jupyter Notebook integration capability within WebGME. Our collaborators at Fujitsu are developing similar tools for cybersecurity research - based on the WebGME platform.
EDUCATIONAL ADVANCES:
None, during this reporting period.


