 Policy Analytics for Cybersecurity of Cyber-Physical Systems: October 2020 (Y3, Q2)
Policy Analytics for Cybersecurity of Cyber-Physical Systems: October 2020 (Y3, Q2)
Funding Type: Full proposal
Start Date: March 01, 2018
Expected Completion Date: April 30, 2020
Principal Investigator: Nazli Choucri
Public View
Accomplishments
Accomplishments during this reporting period: July 31, 2020 - October 2020 (Year 3: Quarter 2) are presented according to the contents below.
Table of Contents
1. Project Overview
1.1 Problem & Purpose
1.2 Research Design
1.3 Database in Text Form
2. Review of Method - Simplified
2.1 Cumulative Steps
3. Year 3 - Work Plan
3.1 Tasks for Year 3, Quarter 2
4. Tasks Completed in Year 3, Quarter 2
4.1 Network View of NIST "Conceptual Model" of Smart Grid - in NIST 7628
5. Value of Note on Relevance to Enterprise
6. Program Outreach Activities
6.1 Cybersecurity Course
6.2 Presentation to Industry Partner of MIT Sloan School Cybersecurity CAMS Program
7. Publications
7.1 Complexity of International Law for Cyber Operations (Manuscript)
7.2 CyberIRworld: Knowledge System for Science, Sustainability & Policy (Website)
8. References
1. Project Overview
This Quarterly Report can best be understood in the context of the overall project objectives - problems and purpose. Table 1 shows an overview of the project.
| Table 1. Project Overview |
|
|
1.1 Problem & Purpose
Policy documents, guidelines, directives, and regulations are routinely presented in text form, page-by-page and word-by-word, and supported by figures, diagrams, and tables as needed. Rooted in legal tradition, this practice reinforces a linear logic, usually with a checklist for meeting requirements.
The paradox is that the text form is an impediment to the implementation of policies and directives and creates opportunity costs. Below are generic opportunity costs as text-based policy documents. See Table 2.
Note that while our applications for method development and testing focus on one complex pervasive cyber-physical system - smart grid for electric power systems - the problem defined and the methods developed are generic in form.
| Table 2. Opportunity Costs |
|
|
This project supports the national strategy for cybersecurity, as outlined in Presidential Executive Orders (EXORD) [1-2] and the National Defense Authorization Acts (NDAAs) [3-5]. The focus is situated on users and the Cybersecurity Framework (CSF) [6] in order to facilitate access to, and the use of, CSF
The Cybersecurity Framework is mandatory in the public sector (See [1]) and greatly encouraged for the private sector. However, the mission-specific application is left to the user - with only general guidance provided by CSF directives. The goal is to provide tools to facilitate policy implementation. Operationally, our goal is to develop analytics for cybersecurity policies and guidelines designed to:
a. Extract knowledge embedded in policy guidelines,
b. Explore implications of policy directives, and
c. Reduce, if not eliminate, the opportunity costs shown in Table 2.
1.2 Research Design
The research design is in modular terms and anchored in a structured model of properties for complex cyber-physical systems. The design and analyses are generic in the sense that they are relevant to, and provide insights for, the cybersecurity of various complex cyber-physical systems. Figure 1 presents a simplified view.
| Figure 1. Overall Project Design - Simplified |
|
|
1.3 Database in Text Form
Figure 2 identifies, once more, the documents whose text constitute the "raw data" for this project. The logic for this selection is provided in previous reports.
| Figure 2. Smart Grid Cybersecurity Directives |
|
|
2. Review of Method - Simplified
2.1 Cumulative Steps
The refinement of the research design in Year 2 yielded a robust proof-of-concept for both the content and sequence of steps in our analytics for policy. Method is essential for any application. In principle, it must be completed before it is customized for a specific enterprise. In practice, however, both early results and knowledge generated help to improve the overall design. In this project, the work evolved into specific, but often overlapping, tasks:
a. Text-to-Data
b. Data-to-Framework
c. Framework-to-Metrics
d. Metrics-to-Model
e. Model-to-Analytics
3. Year 3 - Work Plan
Overall, tasks in Year 3 are designed to examine system structure and process of information flows, technical architecture, and system management, focusing on (i) Framework-to-Metrics and (ii) Metrics-to-Model. Specifically, the goal is to:
a. Analyze in detail the system-wide structure and information flows,
b. Generate visual representations of structure and information flows using graph theory and network models & methods,
c. Use these representations to identify critical nodal or control points (direct or indirect) that may be targets for policy or targets for unwanted interventions, and to the extent possible,
d. Distinguish between factors related to human/management versus technical operations/connections.
3.1 Tasks for Year 3, Quarter 2
Quarter 2 focuses on generating visual representations for the reference case, as well as comparative policy analysis - using graph theory and network methods. The goal is to:
a. Create a base network model of the DSM, and,
b. Use the network to:
i. Identify and examine the implications of C-I-A security objectives, as well as the Impact levels and Security Requirements for nodes & logical interfaces, and
ii. Identify the relevant NIST Cybersecurity Framework functions based on the Impact level.
4. Tasks Completed in Year 3, Quarter 2
4.1 Network View of NIST "Conceptual Model" of Smart Grid - in NIST 7628
Figure 6, below, shows the network model of the NIST 7628 smart grid system ("as-is") derived from metrics in the design structure matrix (Figure 5). Note the color-coding, which identifies what NIST labels as "actors" within the system.
| Figure 6. Network Model of NIST 7628 Smart Grid "Conceptual Model" |
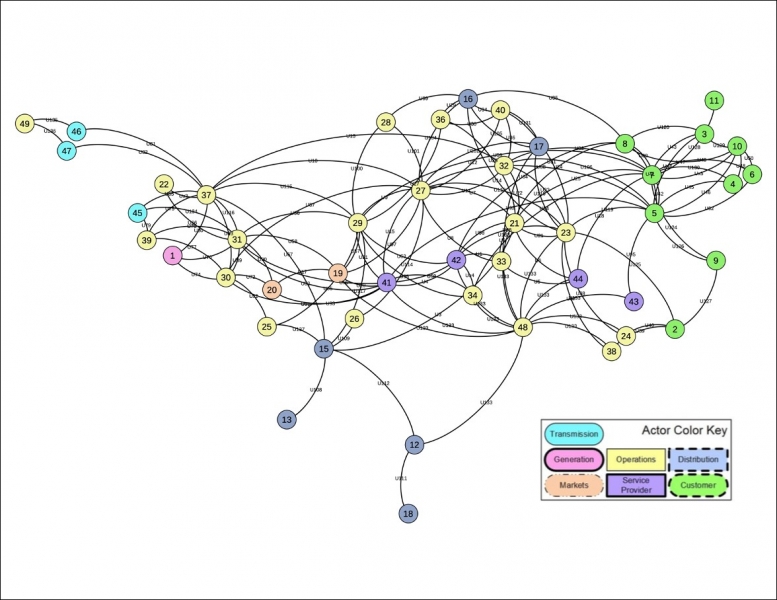 |
The network system in Figure 6 is itself a data-based model. It serves as a reference model and a "laboratory" for situating, understanding, and pursuing the implementation of CSF directives. We then identified the distribution of CSF impact levels and security objectives (C-I-A) throughout nodes and zones for the reference network view of the NIST 7628 smart grid model, for each of the "actors" in the overall system. Note that CSF and related documents provide - in text and table forms - the information presented.
5. Value of Note on Relevance to Enterprise
An earlier report signaled the potential benefits of this work for an enterprise. To this, we add that if an enterprise uses our linked database and seeks to customize the results to its own properties, then it must incorporate enterprise-specific knowledge into the essential structure of cybersecurity directives. This means that an enterprise must:
a. Map its own system to the NIST "as-is" system. Given that our work is based on a sector-independent framework and guideline documents, any enterprise that intends to use the work will need to map its own system components and policies to the relevant reference documents.
b. Identify system specific vulnerabilities. Based on the above mapping, an enterprise will also need to develop an assessment of the threat landscape, as well as the vulnerabilities identified, and known by, the system owners.
The methods we develop, and the tools provided, would greatly facilitate the tasks of the enterprise.
6. Program Outreach Activities
6.1 Cybersecurity Course
The new course on Cybersecurity focuses on multidisciplinary approaches to sources, types, and impacts of cyber threats. Attention is given to operations & solutions strategies in technical, economic, political and strategic contexts. The structure is as follows:
Part I - Overview of cybersecurity theory, policy, practice. Our approach is to draw on multiple perspectives and focus on the diversity of threats, intents, capabilities, and policy challenges.
Part II - Geostrategic, political & economic "realities" of cybersecurity; new markets with new vectors; cases, simulation, data & metrics, agency and actors, gains & losses.
Part III - Policy responses to changing complexities of cyber threats; alternative futures for key entities; implications for social and global systems.
6.2 Presentation to Industry Partner of MIT Sloan School Cybersecurity CAMS Program
We presented the results of our research to date on the problems that the text form creates for implementation policies and guidelines. We reviewed the research design and illustrated ways in which problems of policy-as-text can be addressed in order to facilitate policy implementation.
7. Publications
7.1 Complexity of International Law for Cyber Operations (Manuscript)
The pre-study - which served as a 'test-case' for the initial phase of the MIT project - is the analysis of a single document, namely Tallinn Manual 2.0 (https://ccdcoe.org/research/tallinn-manual/). The pre-test is now complete.
- A pre-publication copy is available upon request. Preliminary results were presented at the 2019 Summer SoS Quarterly conference (see slides 32-34 available at https://cps-vo.org/node/61617).
Only indirectly connected to this pre-lablet, our research on the effects of temporality on cyber acquisition is reported in:
- Pre-publication of T. Klemas (USAF), S. P. Atkins (USAF and MIT), N. Choucri (MIT) and R. Liverly (USAF), "Accelerating Cyber Acquisitions: Introducing a Time-Driven Approach to Manage Risk with Less Delay," is available at the MIT Department of Political Science Newsletter (Submitted October 1, 2020).
7.2 CyberIRworld: Knowledge System for Science, Sustainability & Policy (Website)
One of the tasks identified in Year 1 - the construction of an internally consistent structure to organize, metricize, and manage critical information - initially focused on collecting data relevant to the Smart Grid system. We identified the need for a broader logical system to organize, metricize, and manage critical information - well beyond the Smart Grid - that can be of use for the wider SoS community.
We now present CyberIRworld, an ontology-based knowledge system characterized by the identification and extraction of, and connections among, content rich, quality-controlled quantitative and qualitative information. The ontology focuses on four domains, or systems of interaction:
1. Cyber-International Relations (Cyber-IR);
2. Governance of, and Institutions for, Cyber-IR;
3. Cyber-IR Conflict and Warfare; and
4. Cybersecurity and Sustainability.
Each domain is then differentiated into four dimensions of the system state:
1. "As-is" system state,
2. System problems,
3. Technological solution strategies, and
4. Socio-economic solution strategies.
We expect that a functional website will be available in early Spring, 2021. For context, see website: https://cyber-ir.mit.edu/cyberworld/what-is-cyberworld.
8. References
[1] U.S. President. Executive Order. "Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure, Executive Order 13800 of May 11, 2017." Federal Register Vol. 82, No. 93 (May 11, 2017): 22391-22397. https://www.federalregister.gov/d/2017-10004.
[2] U.S. President. Executive Order. "Securing the Information and Communications Technology and Services Supply Chain, Executive Order 13873 of May 15, 2019." Federal Register Vol. 84, No. 96 (May 17, 2019): 22689-22692. https://www.federalregister.gov/d/2019-10538.
[3] National Defense Authorization Act for Fiscal Year 2020. Public Law No: 116-92. https://www.congress.gov/bill/116th-congress/senate-bill/1790.
[4] John S. McCain National Defense Authorization Act for Fiscal Year 2019. Public Law No: 115-232. https://www.congress.gov/bill/115th-congress/house-bill/5515/text
[5] National Defense Authorization Act for Fiscal Year 2018. Public Law No: 115-9. https://www.congress.gov/bill/115th-congress/house-bill/2810/text






