 Multi-model Testbed for the Simulation-based Evaluation of Resilience (January '21)
Multi-model Testbed for the Simulation-based Evaluation of Resilience (January '21)
PI(s), Co-PI(s), Researchers:
- Peter Volgyesi (PI)
- Himanshu Neema (Co-PI)
HARD PROBLEM(S) ADDRESSED
This refers to Hard Problems, released in November 2012.
- Security Metrics Driven Evaluation, Design, Development, and Deployment
- Resilient Architectures
The goal of the Multi-model Testbed is to provide a collaborative design tool for evaluating various cyber-attack / defense strategies and their effects on the physical infrastructure. The web-based, cloud-hosted environment integrates state-of-the-art simulation engines for the different CPS domains and presents interesting research challenges as ready to use scenarios. Input data, model parameters, and simulation results are archived, versioned with a strong emphasis on repeatability and provenance.
PUBLICATIONS
Ajay Chhokra, Carlos Barreto, Abhishek Dubey, Gabor Karsai, Xenofon Koutsoukos, "Power-Attack: A comprehensive framework for modeling and simulating attacks in power systems", 14th IEEE PowerTech Conference, June 27th – July 2nd, 2021. Madrid, Spain (submitted)
KEY HIGHLIGHTS
Graph Neural Networks on AWS
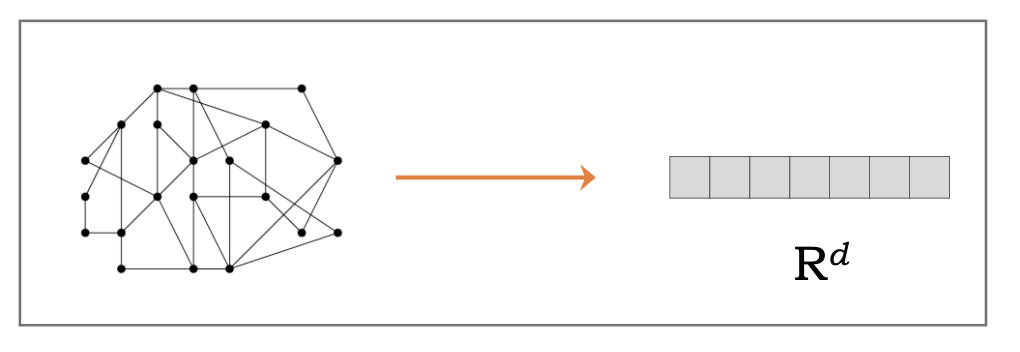
Our current research in developing novel graph descriptor representations is supported by an Amazon Web Services (AWS)-based scalable deployment. This work borrows some ideas from the controllability of Laplacian dynamics and obtains more expressive representations of the graph structure (graph embedding) based on how some phenomenon spreads/propagates/evolves in the structure. Network training and evaluation requires significant computational power, thus we rely on customized on-demand AWS instances to support this effort. Also, we are developing a graph neural network support for DeepForge to create a more accessible design and evaluation environment in this domain.
Deep Learning Testbed Infrastructure
We made significant improvements to DeepForge, our web-based collaborative design and experimentation platform for deep neural network-oriented research. These include:
- Support for reification of artifact provenance as executable pipeline
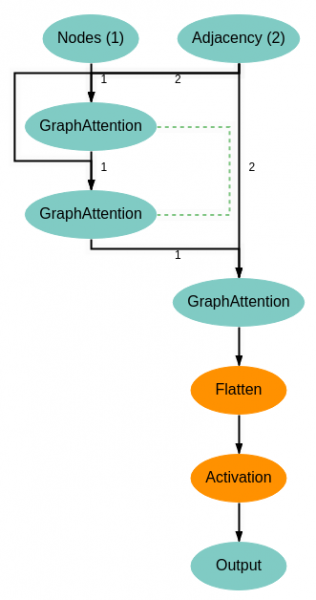
- Graph neural network support (including various graph attention, convolution, and Chebyshev convolutional networks).
- Support for sharing weights between neural network layers.
- Improved performance and scalability of neural network analysis.
- Improvements to plotting capabilities with multiple plots.
- Support for interactively training neural networks.
- Many bug fixes and code cleanup and UI/UX improvements.
Threat Modeling and Risk Analysis in Industrial Control Systems
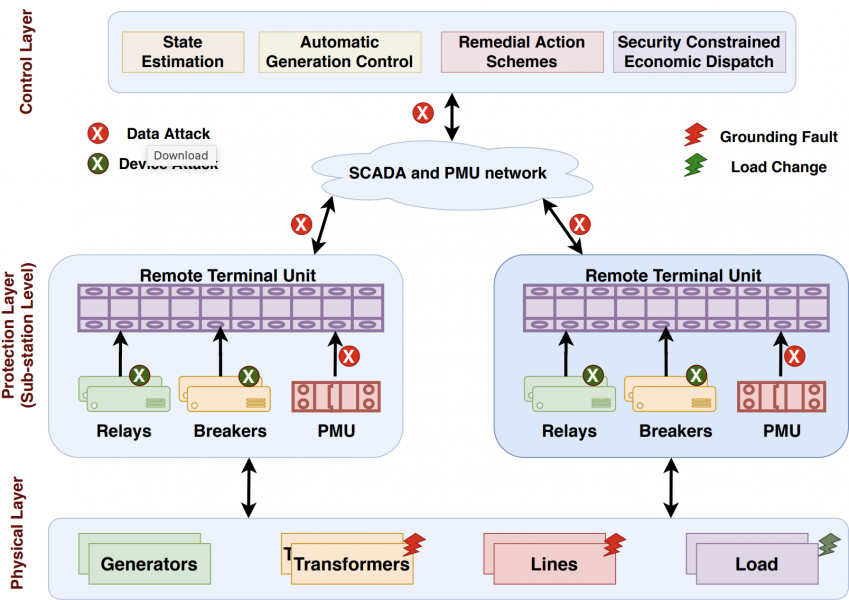
This is an ongoing effort in the development of a modeling and analysis framework for threats and cybersecurity risks in Industrial Control Systems (ICS). Identification of system vulnerabilities and implementation of appropriate risk mitigation strategies are crucial for ensuring the cybersecurity of Industrial Control Systems (ICS). These system vulnerabilities must be evaluated depending on their exploitability, impact, mitigation status, and target platform and environments. Therefore, in order to assess system vulnerabilities and risk mitigation strategies quantitatively, we are focusing on threat modeling and risk analysis methods for the cybersecurity of Railway Transportation Systems (RTS), which are real-world ICS and have become increasing vulnerable to cyber-attacks due to growing reliance on networked physical and computation components. As part of this work, we have already design a novel modeling language that enables modeling of: (a) the physical and network infrastructure of the system, (b) vulnerabilities in system components, (c) component attack trees that describe different ways in which specific component attacks could be carried out, and (d) attack graphs that describe how attacks can propagate across multiple system components. We have also developed a simple analysis tool that is capable of calculating vulnerability propagation within the ICS and automatically generate the component attack trees and system attack graphs. We demonstrated this work to NIST as part of our ongoing collaboration to gain feedback on our approach. The NIST has further demonstrated these ideas and tools to American Association of Railroads (AAR), where we aim to get more subject matter feedback.
Domain-specific language (DSL) for scenario-generation
This is also an ongoing effort and targets data generation through simulations for cybersecurity evaluations and decision support tools for CPS. Our approach involves designing a language to describe cyber scenarios and various parametric and scenario variations and automation tools that sweep these scenario variations for effective scenario and data generation. Our work involves integrating the cyber-attack library in this language for generating cyber scenarios.
Virtual technology workshop with Fujitsu System Integration Laboratories, Ltd., November 4, 2020.
Discussion topics:
- Threat Intelligence - Sharing Policy Enforcement (SPE) for Cyber Threat Intelligence (CTI) documents
- Fujitsu Red Team Studio (using Vanderbilt WebGME)
- Vanderbilt WebGME and Deepforge integration with Fujitsu security testbeds
Collaboration with NIST on threat modeling and risk analysis in ICS, Jan. 2021
Discussion topics:
- Threat modeling in Railway ICS
- Risk Analysis
- Quantitative Risk Evaluation
- Integration with Simulation-Based Evaluation
- Demonstration of railway infrastructure cybersecurity evaluation tools and threat modeling approach to American Association of Railroads (AAR)
EDUCATIONAL ADVANCES and OUTREACH
Dr. Himanshu Neema is continuing to advise three undergraduate students for their Spring internships at our institute. A brief descriptions of these internship projects are provided again below. Please note that these students are working with our technologies, but the internships are not funded by this project.
Local Virtual Power Plant with Transactive Energy
This project aims to evaluate whether transactive energy can provide economic benefit for developing virtual power plants (VPPs) for cities. In VPPs, communities transition from using more electricity for locally generated energy from renewable energy sources such as rooftop solar panels. However, this is highly cost prohibitive and so this project is investigating whether TE can reduce these costs. In addition, the project also aims to evaluate the impact of TE on better management of supply and demand in the DER integrated distribution grid. Recently, our work involves designing fair and robust real-time pricing strategies.
Threat Modeling and Risk Analysis for ICS
This project aims to develop modeling language and analysis tools for CPS. The language is being developed using Vanderbilt's WebGME modeling environment. Using the modeling language one can create system architecture for specific ICS such as railway infrastructure. The system architecture comprises of various components within the system and different types of network connectivity among these components. Further, vulnerability scores could be assigned to various components with regard to different categories of Microsoft's STRIDE threat modeling method. The analysis tools as part of the language could be used to calculate vulnerability scores at the component level. In addition, the visualization tools will help show the generated component attack trees and system attack graphs that directly help with risk analysis of ICS. Recently, our work involves adapting our threat modeling for larger scenario-based risk evaluation of ICS.
Evaluation of Vector Control and Social Policies on Pathogen Spread within Communities
This recently started project aims to utilize agent-based simulations for modeling arthropod behavior and human activities as well as social policies for vector control and for changing human behavior in order to evaluate how these affect the spread of pathogens in humans through mosquito bites. We plan to use integrated simulations for these evaluations. Recently, our work involves integrating various agent-based simulations and related real-world services into a coherrent framework.


