Policy Analytics for Cybersecurity of Cyber-Physical Systems: April 2021 (Y3, Q4)
Policy Analytics for Cybersecurity of Cyber-Physical Systems: April 2021 (Y3, Q4)
Funding Type: Full proposal
Start Date: March 01, 2018
Expected Completion Date: April 30, 2020
Principal Investigator: Nazli Choucri
Public View
Accomplishments
Accomplishments during this reporting period: January 2021 - April 2021 (Year 3: Quarter 4) are summarized in this report.
Table of Contents
1. Project Objectives
1.1 Operational Focus
2. Highlights of Year 3, Quarter 4
2.1 Core "Re-do" Research
2.2 "Re-do" Results
2.3 Burden of "Re-do"
3. Year 3, Quarter 4 Work Plan
4. Imperatives for "Re-do"
5. Outreach
5.1 Complexity of Temporality
5.2 AI-based Risk and Representation of Adversarial Interactions in Multi-system Competition
5.3 Who Gets What, When, Where, and How?
6. References
Tables & Figures
Table 1. Project Overview
Figure 1. Data Linkage Method: Logic and Sequence
Figure 2. NIST Controls in 800:53 Rev. 5
Figure 3. Computed Network View of NIST 800:53 System of Controls
Figure 4. Structured Data for CPS Analytics
Figure 5. Data-to-Framework: Design Structure Matrix
1. Project Objectives
This Quarterly Report can best be understood in the context of the overall project objectives - problems and purpose. For contextual purposes, Table 1 presents an overview of the project.
| Table 1. Project Overview |
|
|
1.1 Operational Focus
The focus is on the Cybersecurity Framework (CSF) [2] and its users in order to facilitate access to, and the use of, CSF. Our goal is to (a) develop analytics for cybersecurity policies and guidelines, (b) assist in understanding the full implications of the guidelines, and (c) facilitate the use of CSF in a wider range of contexts and applications. Operationally, this requires that the research:
- Extract knowledge embedded in policy guidelines,
- Explore implications of policy directives, and
- Enhance the benefits generated by adherence to CSF.
The Cybersecurity Framework is mandatory in the public sector (See [1]) and greatly encouraged for the private sector. However, the mission-specific application is left to the user--with only general guidance provided by CSF directives. The goal is to provide tools to facilitate policy implementation.
Our first-order applications of method-development and testing focus on one complex, pervasive cyber-physical system, namely, the smart grid for electric power systems. However, the problem addressed and the methods developed have wide-ranging applications. We selected the smart grid case study that draws on the reference model developed by NIST. This test bed is selected because of (a) its salience throughout the industry, and (b) the opportunity to build on the extensive work done by NIST. It is an excellent domain application of the Cybersecurity Framework.
2. Highlights of Year 3, Quarter 4
Every phase of the research design is based on the previous ones. This modular and cumulative approach assumes a degree of sustained validity in the database, both "raw" and "derived." If this assumption does not hold, or if there is any disruption in the validity of previous phases, then a "re-do" is required--as relevant.
When NIST issued a fifth revision (Rev. 5) of its document 800:53, it resulted the formal connections, or interfaces, between multiple sources of "raw" data for this project. It also coupled very closely the controls and control families for security and privacy.
Further, this revision raised serious questions about the implications of this new version of 800:53 regarding current NIST perspectives and priorities pertaining to security.
For this project, especially important is the fact that we faced a necessary "re-do" of research steps, and a review of results, with respect to:
- Data Linkage Process [See Figure 1 below]
- Information pertaining to security controls and control families
- An unexpected entanglement between the Security and the Privacy controls, and control families, thereby creating new ambiguities
- Data-based signals that, in the security domain, "everything is related to everything else and to privacy as well"
- Serious impediments to the "reversing the arrows" test and a validation strategy for our research design and results throughout Year 3, Q1-Q3
| Figure 1. Data Linkage Method: Logic and Sequence |
|
|
2.1 Core "Re-do" Research
Overall, this fourth Quarter of Year 3 was devoted to the "re-do" (such that we remain on schedule to this point) as well as to delineating and understanding the implications of the "entanglements" of security and privacy controls for policy implementation of the Cybersecurity Framework, or for any issues for which the use of 800:53 Rev. 5 is called upon or required. This was accomplished effectively.
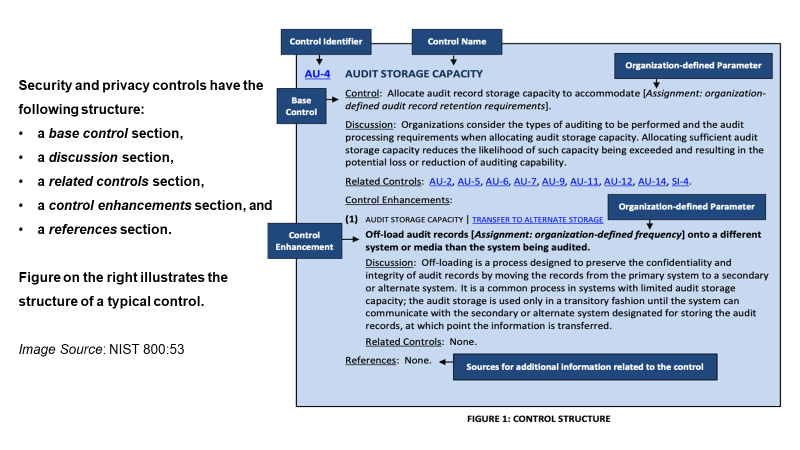
Figure 2 shows the NIST statement on the structure of controls.
| Figure 2. NIST Controls in 800:53 Rev. 5 |
|
|
With the above definitional framework, we proceeded with constructing the DSM for NIST 800:53 Rev. 5--a critical repeat task.
2.2 "Re-do" Results
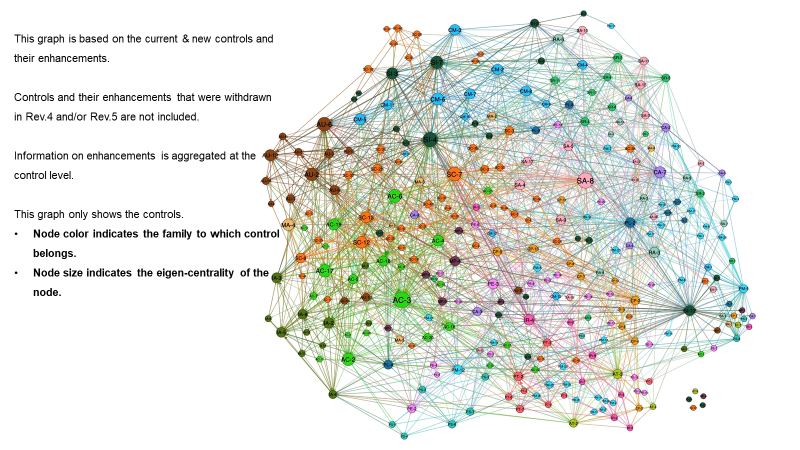
Figure 3 below shows the entire control system and structure of NIST 800:53 Rev. 5. The overarching features are the entanglements, interconnections, and density of controls--spanning both security controls and privacy controls.
| Figure 3. Computed Network View of NIST 800:53 System of Controls |
|
|
2.3 Burden of "Re-do"
The "re-do" created some delays in the completion of several research items that we added to the original proposal and workplan. These additions were identified in terms of (a) providing added validation to the process, (b) expanding the domain uses of our research, and (c) creating value-added for use of the Cybersecurity Framework (CSF).
The most notable additions pertain to the completion of item (a) above, namely, to "reverse the arrow" in Figure 1. This means to go from the user final-requirement "back" up the chain of sequence to the "system as is." This requires use of 800:53 Rev. 5 adapted to the sequence for analysis of "reversal" in Figure 1, that is, from item 6 back to item 1.
This summary can best be understood in the context of the overall research design and the work done in the previous quarters of Year 3, addressed in the remainder of this report.
3. Year 3, Quarter 4 Work Plan
A noted in earlier Quarterly Reports, the tasks in Year 3 are designed to examine system structure and process of information flows, technical architecture, and system management, focusing on (i) Framework-to-Metrics and (ii) Metrics-to-Model. Specifically, the goal is to:
a. Examine in detail the system-wide structure and information flows,
b. Generate visual representations of structure and information flows using graph theory and network methods and models,
c. Use these representations to identify critical nodal or control points (direct or indirect) that may be policy targets, and to the extent possible,
d. Distinguish between factors related to human/management versus technical operations/connections.
The use of NIST 800:53 Rev. 4 provided the data that served the connectivity functions. That function allows us to connect across documents as relevant. The NIST revision to 800:53 Rev. 4 necessitated our "re-do" activities.
4. Imperatives for "Re-do"
Recall that Year 3, Quarter 1 focused largely on task design and pre-testing for the rest of the year. In addition, we identified, empirically, key properties of the logical interfaces for the system "as-is" - following CSF directives - namely:
i. Impact Levels for each Confidentiality, Integrity, and Availability security objective (C-I-A),
ii. Security Requirements based on Impact level for each C-I-A security objective,
iii. CSF functions based on Impact Level.
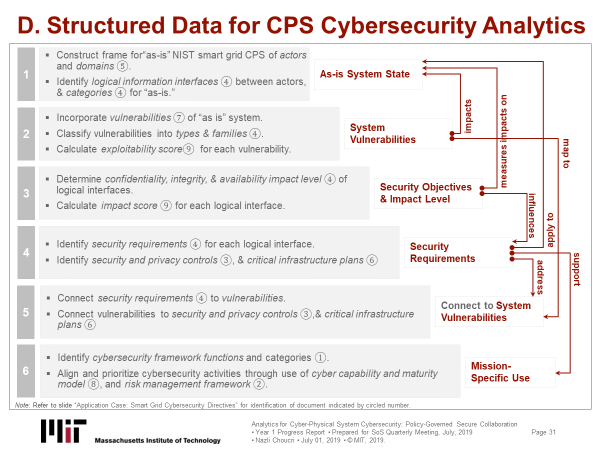
This work enhanced and enriched our database. Figure 4 situates these directives, once more, in the overall research design for data development.
| Figure 4. Structured Data for CPS Analytics |
 |
Also, recall that Year 3, Quarter 2 focused on generating visual representations for the reference case, as well as comparative policy analysis - using graph theory and network methods. The process was established to:
a. Create a complete base network model of the DSM, and,
b. Use the network model to:
i. Identify and examine the implications of C-I-A security objectives, as well as the Impact levels and Security Requirements for nodes & logical interfaces, and
ii. Identify the relevant NIST Cybersecurity Framework functions based on the Impact level.
Earlier reports presented the DSM of the NIST smart grid reference model that serves as the foundation for subsequent analytical work. We show the smart grid DSM model below in Figure 5, once again, as it represents the system state that is to be connected to other components. This is important for contextual purposes, as we proceed with the "re-do."
| Figure 5. Data-to-Framework: Design Structure Matrix |
 |
Shown in an earlier report, the DSM in Figure 5 consists of the system state that is to be connected to the other critical features, noted above. We were on schedule, and ready to connect the DSM to the critical features extracted from the documents ("raw" data). The steps above, completed earlier in Year 3, would, in principle, have enabled us to:
a. Identify critical control points for each node & logical interface based on the:
i. Centrality of nodes based on logical interfaces.
ii. Calculation & consolidation of impact scores for each C-I-A security objective.
b. Locate and consolidate security requirements for each C-I-A security objective.
c. Create representations of additional data generated in (c) and (d) for both DSM and network views.
Given that all data connections required were provided by NIST 800:53 Rev. 4, the construction of Rev. 5 created a new and entirely unforeseen imperative, namely, the need for a "re-do" of the fundamentals for creating connections among the diverse data sources.
The "re-do" is necessitated by the fact that NIST provided a new version of 800:53 labeled Rev. 5. The related imperative is itself an added challenge, namely, to identify the differences between Rev. 5 and Rev. 4 for the purposes of:
a. Understanding content and implications, and
b. Designing and implementing a "re-do" strategy.
Operationally, the major task in the "re-do" involved generating the 800:53 Rev. 5 Design Structure Matrix (DSM) for linkage purposes in order to create its own basic network view. This is the one document that provides the connection across the "re-do" activities required. The initial results - yet to be validated - indicate that both privacy and security controls are heavily dependent with each other.
As indicated in section 2 above, the new results for Rev. 5 are very different from the results of Rev. 4, where privacy controls are added (in "band-aid" form) as an annex to the document.
This "re-do" was also essential for the work we had done on "reversing the arrows" in Figure 1 above, i.e. starting from the last step and working "backward" to the first step. This is a new segment of the research design, which we have developed for two reasons:
a. As a validation check, and
b. As means to provide researchers with alternative ways of addressing core linkage issues, in other words, if the method we have developed "works one way," let us figure out if it "works the other way as well."
5. Outreach
As part of our outreach, the team has contributed three potential suggestions for hard problems, focusing on:
5.1 Complexity of Temporality
The variable of "time" and its diverse attributes shape outcomes in ways not yet fully understood. So, too, different systems of (or in) different domains of interaction operate at different time frames. By the same token, temporal salience is perceived differently under high stress conditions for decision and action, versus perceptions in "routine" situations.
Developing methods to capture and formalize the "role," functions, or impacts of temporality (and changes thereof) is especially critical in adversarial or competitive situations, within and across systems of interaction.
It is evident that the properties of time in geopolitical contexts are well known. Far less clear are the variations in temporality for the environmental consequences of human action, or for environmental impacts on human behavior. With near instantaneity, the time variable in cyber "space" (constructed with the Internet as its current core) must now be taken into account and embedded in all analyses of national security at all levels of analysis. Capturing temporality is an important emergent dynamic challenge, and a new very hard problem.
5.2 AI-based Risk and Representation of Adversarial Interactions in Multi-system Competition
We know that the success of AI in applications to physical and/or engineering systems is much greater than in human-driven systems, where framing risk shapes decision parameters and is subject to intent and capability. AI representation of strategic interactions must draw on advances in computational social sciences to include salient facets of human behavior under stress. This is imperative to AI representation and the investigation of adversarial interactions and actions in competition over military equipment, expenditures, or other manipulable indicators of response.
It is important to develop AI-based methods to account for human behavior and decision-making in strategic settings, characterized mainly by the dynamics of action-reaction. All of this is well documented in the analytics of classic arms, from Richardson to the present. This issue is not the conventional man-machine AI challenge, rather it is one of human behavior-decision, based on intents (human) and capabilities (machine).
When competitive challenges occur or are framed in overlapping multi-systems, as is generally the case with strategic interactions in international relations, the scale and scope of AI algorithms, their derivation and validation are particularly daunting. This is a generic challenge Seldom is strategic competition limited or restricted to a designated system.
Invariably, "spillover effects" expand strategic competition across domains of activity and systems of interaction. More recently, we are observing "spillovers" across cyber and "real" systems. In short, such "spillover" is generally the rule rather than the exception, and requires, by necessity, the multi-system analyses.
5.3 Who Gets What, When, Where, and How?
Competition for control over the Internet and related cyber assets worldwide is already a policy concern. Recent EXORDS and other Presidential directives, as well as previously-leaked emails from WikiLeaks, suggest an active U.S. policy issue regarding the: (a) extent of control and operation of cyber assets in the U.S. by foreign actors, (b) reach of cyber asset control by other states, worldwide, and (c) ability to situate and manage critical control points essential for U.S. national security and global stability.
These are examples of the importance of developing methods focused on the "long chain" of global infrastructure--each operating under different legal, technical, and other regimes or practices. However, its complicated nature and the vastness of dependencies of multiple actors/assets/operations limits the timely availability of information to decision-makers for the security of critical global cyber-physical assets--with implications for policy making, procurement/acquisitions, operation, maintenance.
While the problem could be addressed through the current five hard problems, it can be done only in fragmented parts--not as an integrated or dynamic whole-system. There is a need to consider "Who Gets What, When, Where, and How" which, on scientific grounds, constitutes a new hard problem.
6. References
[1] U.S. President. Executive Order. "Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure, Executive Order 13800 of May 11, 2017." Federal Register Vol. 82, No. 93 (May 11, 2017): 22391-22397. https://www.federalregister.gov/d/2017-10004.
[2] National Institute of Standards and Technology (NIST). 2018. Framework for Improving Critical Infrastructure Cybersecurity. Version 1.1. https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf