Policy Analytics for Cybersecurity of Cyber-Physical Systems: October 2021 (Y4, Q2)
Policy Analytics for Cybersecurity of Cyber-Physical Systems: October 2021 (Y4, Q2)
Funding Type: Full proposal
Start Date: March 01, 2018
Expected Completion Date: April 30, 2020
Principal Investigator: Nazli Choucri
Public View
Accomplishments
Accomplishments during this reporting period: July 2021 - October 2021 (Year 4: Quarter 2) are summarized in this report.
Table of Contents
1. Project Objectives & Research Design - Brief Reminders
1.1 Overview of Design
1.2 Specific Result(s) of Y4, Q2
2. NIST as "Laboratory"
2.1 Project Database
2.2 Cybersecurity Framework
2.3 Essential Data Linkages
3. Year 4, Quarter 2: Where are Threats and Impacts?
3.1 Embedded Knowledge
3.2 Operational Analytics
4. System-Wide Salience State
5. Publications
5.1 Complexity of International Law for Cyber Operations
5.2 A Systematic Framework to Understand Transnational Governance for Cybersecurity Risks from Digital Trade
Tables & Figures
Table 1. Project Overview -- Reminder
Figure 1. Overall Project Design -- Simplified View
Figure 2. "Raw Data Base:" Smart Grid Cybersecurity Policy Directives
Figure 3. Embedded Knowledge: Multiple Perspectives on Cyber-Physical System
Figure 4. Operational Analytics: Methods for Analyzing Smart Grid Cybersecurity
Figure 5. Eigenvector Centrality of the Nodes
1. Project Objectives & Research Design - Brief Reminders
As a reminder, the hard problem addressed in this Project is policy governed secure collaboration. Each word serves as a key anchor. This Quarterly Report for Year 4, Quarter 2 can best be viewed as a follow-up to the results in Y4, Q1. Table 1 provides, again, an overview of the entire research initiative.
| Table 1. Project Overview - Reminder |
|
|
Previous quarterly reports addressed accomplishments for each reporting period. These included:
1. Our principles as responsible researchers and implications for the Project;
2. Some examples of practical uses of our investigations; and
3. Data-related operational disruption that required major "re-do" efforts.
At this point, we do not reiterate the information above - on the understanding that readers would be familiar and take these into account as they consider the research results for the current reporting period.
1.1 Overview of Design
The overall research design for the project as a whole is:
- Modular in structure, and
- Anchored in a Model of properties for complex cyber-physical systems.
In earlier Quarterly Reports we also reported on the details of research to this point. The design and analyses are framed in generic terms, and the analytics developed are generic as well, in the sense that they are not idiosyncratic to the test-bed we have employed. As a reminder, Figure 1 presents a simplified view of the research design, and assists in highlighting the activities of Phase 4.
| Figure 1. Overall Project Design - Simplified View |
|
|
Every phase of the design is based on the research and results of previous phases. But it is not linear in the sense that there is embedded feedback in structure and process. We generally replicate all tasks that involve direct human intervention. Recall that in the previous report (Y4, Q1), we focused on the imperatives of the "re-do" due to a shift in NIST content in a new publication that superseded the materials upon which we based our initial research.
1.2 Specific Result(s) of Y4, Q2
We know that a large number of requirements are needed to ensure cybersecurity for any cyber-physical system. In this reporting period we provide a method to answer the following questions:
Where should an industry or operator of a cyber-physical system focus in order to improve cybersecurity conditions? Where are the critical vulnerabilities? What should be prioritized for securing the system?
There are examples of the questions for which our new methods - to draw on NIST as a "Laboratory" - can be put to good use.
2. NIST as "Laboratory"
Of the many powerful contributions provided by NIST over the years, we find its role as a "laboratory" to be extremely important and understated. In the previous quarterly report, we signaled the specific features of this "laboratory" as a "test-bed" for cybersecurity policy of smart grid as a cyber-physical system. Recall that the focus on this test-bed was selected because of its:
1. Salience throughout the industry and society,
2. Complexity as a cyber-physical system, and the opportunity to build on the extensive work done by NIST,
3. Excellence as a domain of research on analytics for cybersecurity policy of cyber-physical systems, and as a "laboratory."
In addition, as noted in earlier Quarterly Reports, given that the Cybersecurity Framework (CSF) is mandatory in the public sector and greatly encouraged for the private sector, the CSF directives for policy implementation require use of identified and identifiable tools.
However, the mission-specific or industry-specific application is left to the user - with only general guidance provided by CSF directives.
NIST as "Laboratory" enables us to:
1. Develop analytics for cybersecurity policies and guidelines,
2. Assist in understanding the full implications of the guidelines, and
3. Provide methods to facilitate use of CSF in diverse contexts and applications.
In addition to critical analytics, there is value added in providing practical ways of making it easier to use CSF.
2.1 Project Database
Below we show, once more, the basic policy documents that serve as the raw data for different phases in the overall project. Each policy document is autonomous - i.e. on a standalone basis. However, depending on the particular needs of the user - in terms of mission, industry, or other - drawing on other documents can be a necessity, not a choice (The specific number that precedes the name of each autonomous directive in Figure 2 serves as an identifier of the data used at different points in the Project).
| Figure 2. "Raw Database:" Smart Grid Cybersecurity Policy Directives |
|
|
2.2 Cybersecurity Framework
We recognize that effective use of CSF requires that users:
- Extract knowledge and guidelines embedded in diverse policy documents;
- Explore the full implications of policy directives for cybersecurity of cyber-physical systems;
- Identify the CSF directives relevant to their "case," and locate the operational documents to guide implementation.
In short, the above i - iii are necessary in order to capture and enhance the uses of the Cybersecurity Framework.
2.3 Essential Data Linkages
The full value of CSF can be difficult to capture given (a) the set of intervening tasks required and (b) the distributed nature of the database. CSF points to what has to be done and why, but not how. It is up to the user to work through the process outlined by CSF. Pointers to steer users to other (different) documents are provided in order for users to take next steps.
In this Project, operational use is created by providing a method to streamline access to, and use of, essential data required to implement the security-related actions required by CSF. Because CSF points to a number of individual documents hosting different directives, the users' task is to identify and make connections among them as needed. Moreover, modifications and updates by NIST on the content of key intervening documents require users, in turn, to identify the updates and determine requirements for change.
3. Year 4 Quarter 2: Where are Threats and Impacts?
3.1 Embedded Knowledge
In Figure 3 below we highlight the simple but important observation: the same cyber-physical system can be subject to different forms of threats and impacted in different ways. The challenge is to:
1. Capture the salient range thereof,
2. Differentiate among them by degree or other criteria of vulnerability, and
3. Decide what the priority remedial or protective actions should be.
| Figure 3. Embedded Knowledge: Multiple Perspectives on Cyber-Physical System |
|
|
3.2 Operational Analytics
We now focus, as shown in Figure 4 below, on:
1. Identifying relative salience,
2. Situating relative impacts, and
3. Applying three criteria, namely, the security objectives
| Figure 4. Operational Analytics: Methods for Analyzing Smart Grid Cybersecurity |
|
|
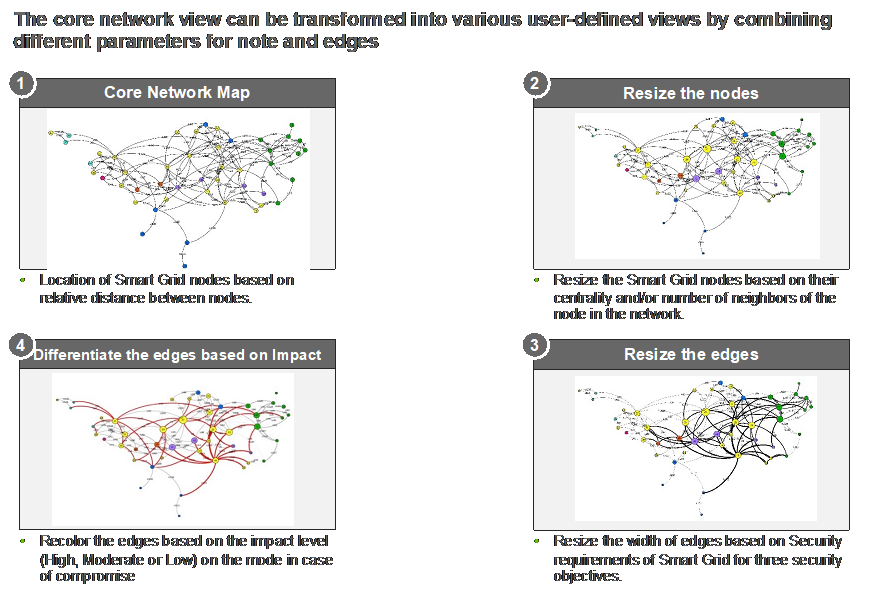
4. System-Wide Salience State
Extending the above, we now turn to a broader system-wide view of the structure and composition of the base network view of the smart grid.
Figure 5 below differentiates the nodes in terms of their relative centrality to the system as a whole. This provides an initial signal to the user (industry or operator) of critical value to be protected.
| Figure 5. Eigenvector Centrality of the Nodes |
|
|
Notes: Spatial distance between two actors based on actor importance and distance to others; Nodes represent actors; node color represents domain to which an actor belongs; node size represents eigenvector centrality of a node in the network. The bar chart inset identifies the most salient nodes in the system.
5. Publications
5.1 Complexity of International Law for Cyber Operations
This paper is scheduled to be presented at the forthcoming 20th IEEE Symposium on Technologies for Homeland Security (HST 21), which will be held November 8-9, 2021 as a virtual conference. The paper is part of a project research update discussed at the Kansas SoS meeting.
Authors: Nazli Choucri and Gaurav Agarwal
Abstract: Policy documents are usually written in text form - word after word, sentence after sentence, page after page, section after section, chapter after chapter - which often masks some of their most critical features. The text form cannot easily show interconnections among elements, identify the relative salience of issues or represent feedback dynamics, for example. These are "hidden" features that are difficult to situate. This paper presents a computational analysis of Tallinn Manual 2.0 on the International Law Applicable to Cyber Operations, a seminal work in International Law. Tallinn Manual 2.0 is a seminal document for many reasons, including but not limited to, its (a) authoritative focus on cyber operations, (b) foundation in the fundamental legal principles of the international order, and (c) direct relevance to theory, practice, and policy in international relations. The results identify the overwhelming dominance of specific Rules, the centrality of select Rules, the Rules with autonomous standing (that is, not connected to the rest of the corpus), and highlight different aspects of Tallinn Manual 2.0, notably situating authority, security of information - the feedback structure that keeps the pieces together. This study serves as a "proof of concept" for the use of computational logics to enhance our understanding of policy documents.
5.2 A Systematic Framework to Understand Transnational Governance for Cybersecurity Risks from Digital Trade
Authors: Choucri, N., Madnick, S., Huang K., and Zhang, F. (2021) "A Systematic Framework to Understand Transnational Governance for Cybersecurity Risks from Digital Trade." Global Policy (Durham University and John Wiley & Sons Ltd.): pp: 1-14.
Abstract: Governing cybersecurity risks from digital trade is a growing responsibility for governments and corporations. This study develops a systematic framework to delineate and analyze the strategies that governments and corporations take to address cybersecurity risks from digital trade. It maps out the current landscape based on a collection of 75 cases where governments and corporations interact to govern transnational cybersecurity risks. This study reveals that: first, governing cybersecurity risks from digital trade is a global issue whereby most governments implement policies with concerning that the cybersecurity risks embedded within purchasing transnational digital products can influence their domestic policies and societal systems. Second, governments dominates the governance interactions by implementing trade policies whereas corporations simply comply. Corporations do, however, have chances to take more active roles in constructing the governance system. Third, supply chain cybersecurity risks have more significant impacts on governance mode between governments and corporations, whereas concerns on different national cybersecurity risks do not. Fourth, the interactions between governments and corporations reveal the existence of loops that can amplify or reduce cybersecurity risks. This provides policy implications on transnational cybersecurity governance for policy makers and business leaders to consider their potential options and understand the global digital trade environment when cybersecurity and digital trade overlap.