Policy Analytics for Cybersecurity of Cyber-Physical Systems: January 2022 (Y4, Q3)
Policy Analytics for Cybersecurity of Cyber-Physical Systems: January 2022 (Y4, Q3)
Funding Type: Full proposal
Start Date: March 01, 2018
Expected Completion Date: April 30, 2023
Principal Investigator: Nazli Choucri
Group View
Accomplishments
Accomplishments during this reporting period: October 2021 - January 2022 (Year 4: Quarter 3) are summarized in this report.
Table of Contents
1. Project Problem and Objectives
1.1 Problem
1.2 Analytics for Policy: Toward Policy Protocol
1.3 Cyber Security Framework: Test Case
2. Project Review & Contect for Year 4 Quarter 3 Report
2.1 Database -- Policy Texts-as-Raw-Data
2.2 Capturing Value of Policy
3. Fundamentals of Analytics for Policy -- Methods
3.1 Research Challenges
3.2 Operational Imperitives of Policy Linkages
3.3 Situating Relative Impacts of Security Objectives
4. Year 4, Quarter 3 -- Integrated Vulnerability Impacts for Logical Interfaces
4.1 About CVSS
4.2 Toward Consolidated System Security
5. Next Steps
5.1 Assessment of security requirements for logical interfaces (in Y4, Q4)
5.2 Extensions & Policy Protocol
6. Outreach
7. Publications
7.1 Complexity of International Law for Cyber Operations
7.2 A Systematic Framework to Understand Transnational Governance for Cybersecurity Risks from Digital Trade
List of Figures
Figure 1. Overall Project Design -- Simplified View.
Figure 2. "Raw Database:" Key Policy Documents for Application of Cybersecurity Framework to Smart Grid Electrical Power Systems
Figure 3. Smart Grid Network Model
Figure 4. Security Objectives Defined: Confidentiality, Integrity & Availability
Figure 5. Identifying Differentiated Impact Levels of Individual Security Objectives for the test-case: Smart Grid system state "As Is"
Figure 6. NIST Smart Grid conceptual network with edges defining impact level based on CVSS 3.0
Figure 7. NIST Smart Grid conceptual network with edges representing impact level based on CVSS 3.0 & node size indicating centrality scores.
List of Tables
Table 1. Project Overview -- Context.
1. Project Problem & Objectives
The hard problem of this Project is policy governed secure collaboration. The purpose is to develop empirical methods to reduce barriers to operation of cybersecurity policies for cyber-physical systems. The focus is on analytics and applications.
1.1 Problem
The overarching problem-area is three-fold:
Cybersecurity policies are developing faster that their implementation.
- The lag is due in large part to barriers for user-access to guidelines. Operational directives often are located in different documents across the policy eco-system.
- Barriers of any type reduce the value of policies to protect systems (and users) from known vulnerabilities in their operations
Policies are usually articulated and presented in text form.
- Text means word after word, sentence after senctence etc. This form impedes precision and effective targeting to guidelines for "solution" of system "problem"
- Capturing the value of policy depends on the precise representation of system-state and accurate understanding the exisiting vulnerabilities and their impacts.
Such situations require new operational solutions that can become "routine" and "normal".
- Required are analytics for policy targeting specific "directive" or solution to specific system problem-point.
- Effective targeting calls for developing a suite of analytics-for-policy.
The problem-area is not restricted to cybersecurity policies for cyber-physical systems. It is generic, relevant to all policy domains. By the same token, critical elements of solution strategies can be customized to specific contexts.
1.2 Purpose: Analytics for Policy--Toward Policy Protocol
The purpose is to (a) develop methods for on-demand operational use of guidelines and directives, (b) demonstrate with test-case(s), and (c) create a Protocol for Policy analytics.
We have demonstrated in previous reports that effective analytics-for-policy consist of a set of operations, notably:
- Creating metrics for model of system-state of interest
- Transforming policy-texts to data-in-metrics.
- Constructing linked policy ecosystem of cybersecurity guidelines as needed
- Identifying vulnerability impacts on system-state.
- Meeting security objectives by implementing security requirements.
Each item in the set usually consists of several individual but interconnected steps. So far, we completed four of these steps and demonstrated a test-case.
1.3 Cyber Security Framework: Test Case
The test case of analytics for policy is application of the NIST Cyber Security Framework to the smart grid system for electric power. All information pertaining to smart grid systems and operations is derived from NIST"s reference model of smart grid in electric power based on expert panel conclusion. A major challenge is that all guidelines for application of CSF to smart grid systems are distributed across a number of different autonomous policy documents.
The Cyber Security Framework (CSF) points to what has to be done and why. CSF also points to how and where critical information is located in the distributed policy ecosystem. It is up to the user to work through the directives outlined by CSF. In short, NIST provides pointers to steer users to other (different) documents to enable them to take next steps in an overall implementation process. Our project seeks to develop analytics to "cut through" a complex policy architecture.
2. Project Review: Context for Y4 Q3 Report
As a reminder, Table 1 provides, again, an overview of the overall research design. We have completed basic data processing of formal policy documents central to the test case for innovations in analytics.
| Table 1. Project Overview - Context |
|
|
Table 1 presents, once more, a simplified view of the research design. It assists in highlighting the activities of Phase 4 and the results of Y4, Q3 of the current Reporting period.
As signaled earlier, we now concentrate entirely on metrics and models we have derived from the NIST texts pertainingto our test case, the Smart Grid, and to the various and distributed CSF directives.
| Figure 1. Overall Project Design - Simplified View |
|
|
2.1 Database -- Policy Texts as Raw-Data
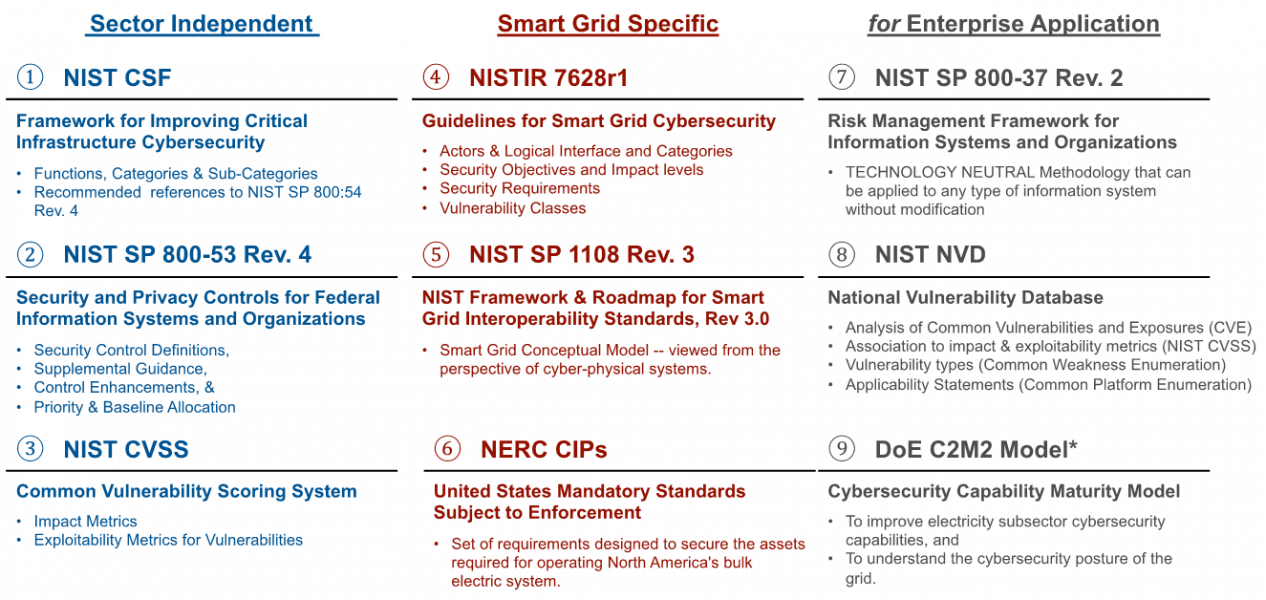
Below we show, once more, the nine policy documents that serve as the raw data for different phases in the overall project. Each policy document is autonomous -- i.e., on a standalone basis. However, depending on the particular needs of the user -- in terms of mission, industry, or other -- drawing on other documents can be a necessity, not a choice.
| Figure 2. "Raw Database:" Key Policy Documents for Application of Cybersecurity Framework to Smart Grid Electrical Power Systems |
|
|
The number that precedes the name of each autonomous directive in Figure 2 serves as an identifier of the data used in the overall research design. Note that some documents are (i) sector independent (ii) others pertain only to the test case, smart grid system specific, and (iii) still others are applicable to specific enterprises.
2.2 Capturing Value of Policy
The full value and implementation of CSF for cybersecurity of smart grid can be difficult to capture given:
-
the details and complexity of smart grid NIST model
-
the set of intervening tasks that are required,
-
the distributed nature of policy documents with information on intervening tasks,
-
the burden on users to manage (a) to (c) and, therefore,
-
the need to create an integrated on-demand method for access to relevant information.
Given that directives for implementation of CSF (Item 1 in Figure 2) are distributed across several individual documents, each hosting different guidelines, the user's task is to identify and make connections among them as needed. Moreover, modifications and updates by NIST on the content of key task-based documents require users, in turn, to identify the updates and determine requirements for making changes to their initially integrated database. The method of integration will be demonstrated further along.
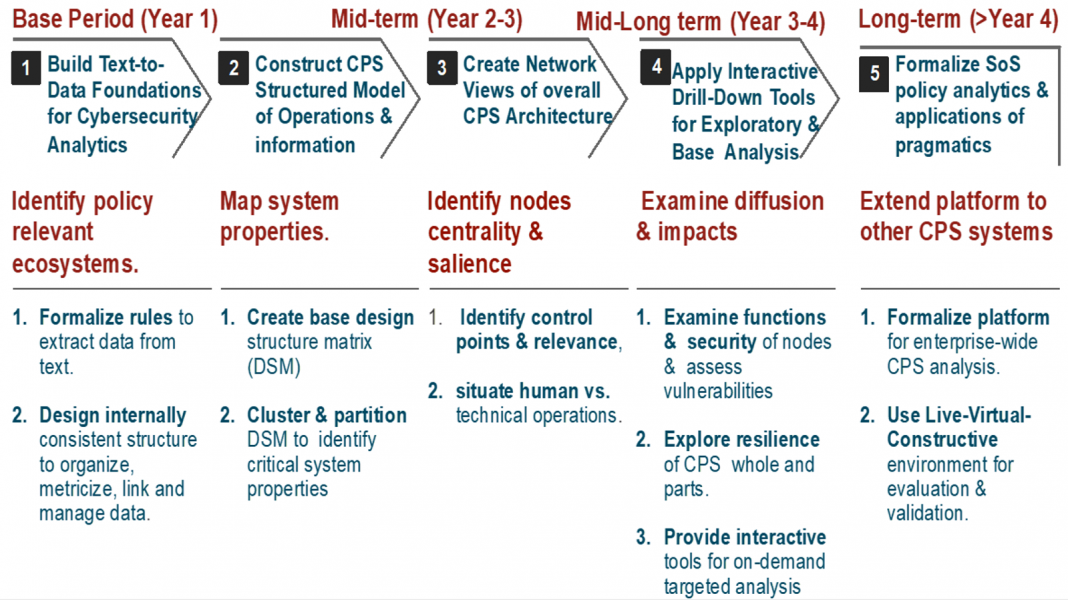
3. Analytics for Policy -- Design of a Protocol
3.1 Project Review & Results
Project review and results consists of FIVE modules. This Report for Y4, Q3 focuses on "FOUR" below. Note that modules ONE to THREE are inputs for FOUR & FIVE.
ONE: Examine one system to generate metrics for analysis of system properties.
RESULT: text-based system properties are transformed into system metrics.
TWO: Generate test-case network system view.
RESULT: network view of system based on metricized properties of test case.
THREE: Construct operational links among relevant policy directives situated in the distributed cybersecurity policy ecosystem system.
RESULT: an integrated database of policy directives stipulated by NIST and other government agencies for implementing CSF on the test case, i.e. smart grid in electrical power systems.
FOUR: Connect the smart grid system properties to NIST estimated vulnerabilities and impacts.
RESULT: identification of differentiated (i) impact levels of vulnerabilities (H, M, L) in the test-case system (ii) by security objective (C,I,A).
** Year 4 Quarter 3 Report focuses on FOUR above.
FIVE: Identify CSF security requirements and connect them to properties of the test-case system.
EXPECTED VALUE enables the user, enterprise, or analyst, to implement CSF directives (and related requirements in Item 2, Item 7, and Item 9) all situated in different policy documents.
3.2 Operational Imperatives of Policy Linkages
The research design requires the construction of operational linkages among data pertaining to system state and CSF policy features. Note: "data" refers to the variables provided by NIST, that we then converted to metrics, as reported earlier.
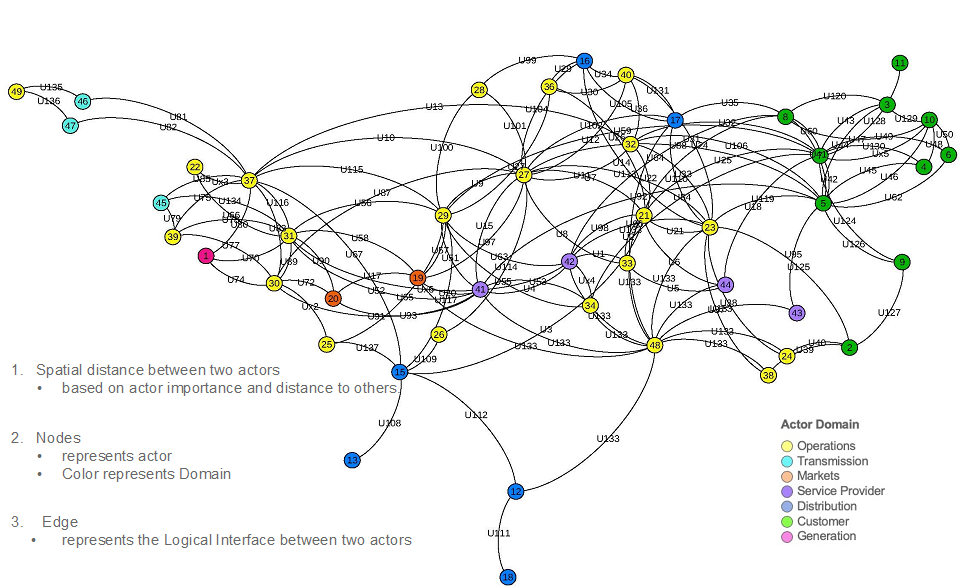
In a previous report we presented the results for the computed base network model of the reference system, i.e. the test case, for the NIST Smart Grid as a cyber-physical system. Recall that the model is derived from the metrics and measures embedded in the Design Structure Matrix representation for the descriptive text of NIST's own Conceptual or Reference Model of Smart Grid, also shown in an earlier report. Figure 3 is a reminder of the base reference network model for the test case.
| Figure 3. Smart Grid Network Model -- Test Case |
|
|
Notes: Spatial distance between two actors (NIST word) is based on node importance and distance to others; Nodes = actors; color = actor domain.
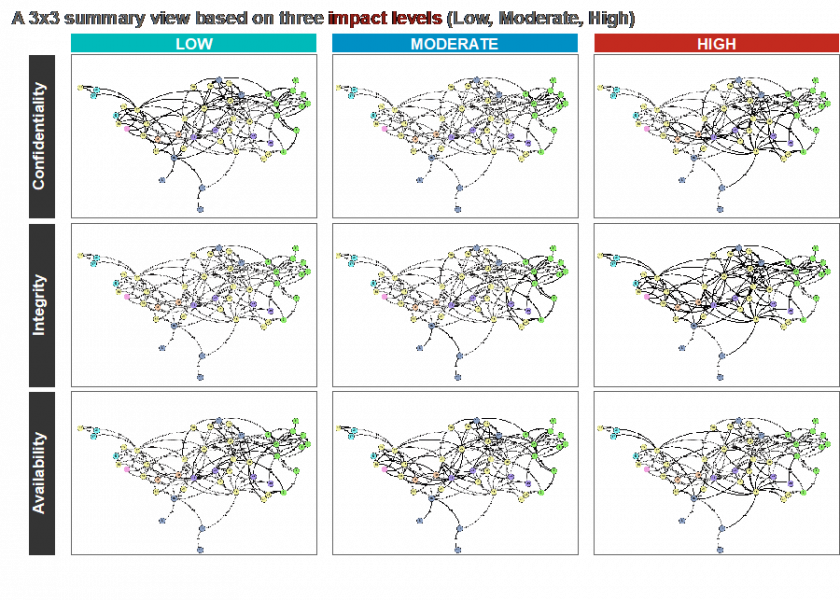
In Q2 of Y4 we computed the system-wide vulnerability impacts for each individual security objective for the test-case, i.e. NIST Smart Grid system. The results reported for Q2 Year 4 are reproduced in the Figure below. There are no shortcuts to addressing the security objectives.
| Figure 4. Identifying Differentiated Impact Levels of Individual Security Objectives for the test-case: Smart Grid system "As Is" |
|
|
Note: Based on data in Guidelines for Smart Grid Cybersecurity-Volume 1," NISTIR 7628 Revision I, September, 2014; doi: NIST.IR.7628r1, p. 76.
Figure 4 above defines the operational challenge of Y4 Q3 Report. While the information in this Figure above is interesting, it is not particularly useful for operational purposes. The figure is too detailed to facilitate effective action.
4. Year 4, Quarter 3: Integrated Vulnerability Impacts for Logical Interfaces
What is needed is a net assessment for vulnerability impacts on the system across three dimensions and three levels of intensity. We now show the consolidation and integration of impact analysis and results shown in Figure 4 (3x3). We compute the vulnerability impacts (3x3) in Figure 4 to generate one net score. The use of CVSS is essential
4.1 About CVSS
CVSS provides a way to capture the principal characteristics of a vulnerability. It is an open framework for communicating the characteristics and severity of software vulnerabilities. CVSS produces a numerical score--ranging from 0 to 10--reflecting its net severity.
4.2 Toward Consolidated System Security
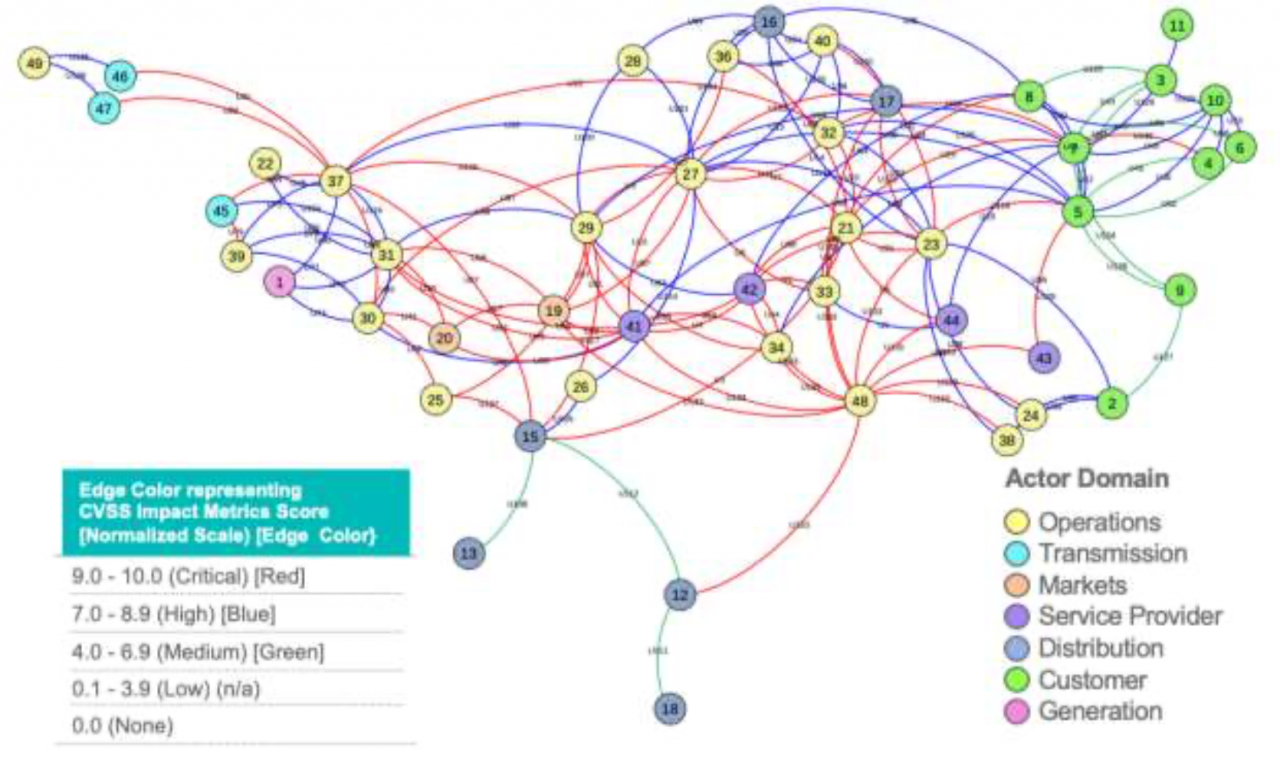
Figure 5 shows the consolidation of analysis and results in Figure 4 (3x3) for Impact levels of system vulnerabilities into one integrated system view.
| Figure 5. Test-Case: NIST Smart Grid: each edge = impact level based on CVSS 3.0 |
|
|
The views in Figure 4 treat all nodes as "being equal" in the system. This is for reference purposes. We also consider centrality score or salience metric for each node in the test case. We also computed the centrality score or salience metric for each node in the test-case, namely NIST smart grid electric power system (not shown here).
5. Next Steps
5.1 Assessment of security requirements for logical interfaces (in Y4, Q4)
Y4 Q4 will focus of security requirements as stated in NISTIR 7628 (item 4 in Figure 2) that are derived from NIST SP 800:53 (item 2 in Figure 2).
5.2 Extensions
The results presented in this report and planned in Q4 of Year 5 anticipate several extensions currently in progress.
6. Outreach
We will combine the outreach activities for the current reporting period with the next period. This is due largely to the connections between activities in these two periods.
7. Publications
7.1 Complexity of International Law for Cyber Operations
This paper was presented at the 20th IEEE Symposium on Technologies for Homeland Security (HST 21), held November 8-9, 2021 as a virtual conference. The paper is part of a project research update discussed at the Kansas SoS meeting.
Authors: Nazli Choucri and Gaurav Agarwal
Abstract: Policy documents are usually written in text form--word after word, sentence after sentence, page after page, section after section, chapter after chapter--which often masks some of their most critical features. The text form cannot easily show interconnections among elements, identify the relative salience of issues, or represent feedback dynamics, for example. These are "hidden" features that are difficult to situate. This paper presents a computational analysis of Tallinn Manual 2.0 on the International Law Applicable to Cyber Operations, a seminal work in International Law. Tallinn Manual 2.0 is a seminal document for many reasons, including but not limited to, its (a) authoritative focus on cyber operations, (b) foundation in the fundamental legal principles of the international order and (c) direct relevance to theory, practice, and policy in international relations. The results identify the overwhelming dominance of specific Rules, the centrality of select Rules, the Rules with autonomous standing (that is, not connected to the rest of the corpus), and highlight different aspects of Tallinn Manual 2.0, notably situating authority, security of information -- the feedback structure that keeps the pieces together. This study serves as a "proof of concept" for the use of computational logics to enhance our understanding of policy documents.
7.2 A Systematic Framework to Understand Transnational Governance for Cybersecurity Risks from Digital Trade
Authors: Choucri, N., Madnick, S., Huang K., and Zhang, F. (2021) "A Systematic Framework to Understand Transnational Governance for Cybersecurity Risks from Digital Trade." Global Policy (Durham University and John Wiley & Sons Ltd.): pp: 1-14.
Abstract: Governing cybersecurity risks from digital trade is a growing responsibility for governments and corporations. This study develops a systematic framework to delineate and analyze the strategies that governments and corporations take to address cybersecurity risks from digital trade. It maps out the current landscape based on a collection of 75 cases where governments and corporations interact to govern transnational cybersecurity risks. This study reveals that: first, governing cybersecurity risks from digital trade is a global issue whereby most governments implement policies with concerning that the cybersecurity risks embedded within purchasing transnational digital products can influence their domestic political and societal systems. Second, governments dominates the governance interactions by implementing trade policies whereas corporations simply comply. Corporations do, however, have chances to take more active roles in constructing the governance system. Third, supply chain cybersecurity risks have more significant impacts on governance mode between governments and corporations, whereas concerns on different national cybersecurity risks do not. Fourth, the interactions between governments and corporations reveal the existence of loops that can amplify or reduce cybersecurity risks. This provides policy implications on transnational cybersecurity governance for policy makers and business leaders to consider their potential options and understand the global digital trade environment when cybersecurity and digital trade overlap.