Biblio
In cyber-physical systems (CPS), sensors and embedded systems are networked together to monitor and manage a range of physical processes through a continuous feedback system. This allows distributed computing using wireless devices. Cyber-Physical Systems—A Computational Perspective examines various developments of CPS that are impacting our daily lives and sets the stage for future directions in this domain.
The book is divided into six sections. The first section covers the physical infrastructure required for CPS, including sensor networks and embedded systems. The second section addresses energy issues in CPS with the use of supercapacitors and reliability assessment. In the third section, the contributors describe the modeling of CPS as a network of robots and explore issues regarding the design of CPS. The fourth section focuses on the impact of ubiquitous computing and cloud computing in CPS and the fifth section discusses security and privacy issues in CPS. The final section covers the role of CPS in big data analytics, social network analysis, and healthcare.
As CPS are becoming more complex, pervasive, personalized, and dependable, they are moving beyond niche laboratories to real-life application areas, such as robotics, smart grids, green computing, and healthcare. This book provides you with a guide to current CPS research and development that will contribute to a "smarter" planet.
It is critical to ensure that network policy remains consistent during state transitions. However, existing techniques impose a high cost in update delay, and/or FIB space. We propose the Customizable Consistency Generator (CCG), a fast and generic framework to support customizable consistency policies during network updates. CCG effectively reduces the task of synthesizing an update plan under the constraint of a given consistency policy to a verification problem, by checking whether an update can safely be installed in the network at a particular time, and greedily processing network state transitions to heuristically minimize transition delay. We show a large class of consistency policies are guaranteed by this greedy heuristic alone; in addition, CCG makes judicious use of existing heavier-weight network update mechanisms to provide guarantees when necessary. As such, CCG nearly achieves the “best of both worlds”: the efficiency of simply passing through updates in most cases, with the consistency guarantees of more heavyweight techniques. Mininet and physical testbed evaluations demonstrate CCG’s capability to achieve various types of consistency, such as path and bandwidth properties, with zero switch memory overhead and up to a 3× delay reduction compared to previous solutions.
If you’re involved in cybersecurity as a software developer, forensic investigator, or network administrator, this practical guide shows you how to apply the scientific method when assessing techniques for protecting your information systems. You’ll learn how to conduct scientific experiments on everyday tools and procedures, whether you’re evaluating corporate security systems, testing your own security product, or looking for bugs in a mobile game.
Once author Josiah Dykstra gets you up to speed on the scientific method, he helps you focus on standalone, domain-specific topics, such as cryptography, malware analysis, and system security engineering. The latter chapters include practical case studies that demonstrate how to use available tools to conduct domain-specific scientific experiments.
- Learn the steps necessary to conduct scientific experiments in cybersecurity
- Explore fuzzing to test how your software handles various inputs
- Measure the performance of the Snort intrusion detection system
- Locate malicious “needles in a haystack” in your network and IT environment
- Evaluate cryptography design and application in IoT products
- Conduct an experiment to identify relationships between similar malware binaries
- Understand system-level security requirements for enterprise networks and web services
Optical Coherence Tomography (OCT) has shown a great potential as a complementary imaging tool in the diagnosis of skin diseases. Speckle noise is the most prominent artifact present in OCT images and could limit the interpretation and detection capabilities. In this work we evaluate various denoising filters with high edge-preserving potential for the reduction of speckle noise in 256 dermatological OCT B-scans. Our results show that the Enhanced Sigma Filter and the Block Matching 3-D (BM3D) as 2D denoising filters and the Wavelet Multiframe algorithm considering adjacent B-scans achieved the best results in terms of the enhancement quality metrics used. Our results suggest that a combination of 2D filtering followed by a wavelet based compounding algorithm may significantly reduce speckle, increasing signal-to-noise and contrast-to-noise ratios, without the need of extra acquisitions of the same frame.
Nowadays, Memory Forensics is more acceptable in Cyber Forensics Investigation because malware authors and attackers choose RAM or physical memory for storing critical information instead of hard disk. The volatile physical memory contains forensically relevant artifacts such as user credentials, chats, messages, running processes and its details like used dlls, files, command and network connections etc. Memory Forensics involves acquiring the memory dump from the Suspect's machine and analyzing the acquired dump to find out crucial evidence with the help of windows pre-defined kernel data structures. While retrieving different artifacts from these data structures, finding the network connections from Windows 7 system's memory dump is a very challenging task. This is because the data structures that store network connections in earlier versions of Windows are not present in Windows 7. In this paper, a methodology is described for efficiently retrieving details of network related activities from Windows 7 x64 memory dump. This includes remote and local IP addresses and associated port information corresponding to each of the running processes. This can provide crucial information in cyber crime investigation.
ABSTRACT: We consider an onlinse optimization problem on a compact subset S ⊂ Rn (not necessarily convex), in which a decision maker chooses, at each iteration t, a probability distribution xover S, and seeks to minimize a cumulative expected loss, 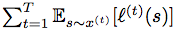 , where ℓ(t) is a Lipschitz loss function revealed at the end of iteration t. Building on previous work, we propose a generalized Hedge algorithm and show a
, where ℓ(t) is a Lipschitz loss function revealed at the end of iteration t. Building on previous work, we propose a generalized Hedge algorithm and show a 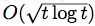 bound on the regret when the losses are uniformly Lipschitz and S is uniformly fat (a weaker condition than convexity). Finally, we propose a generalization to the dual averaging method on the set of Lebesgue-continuous distributions over S.
bound on the regret when the losses are uniformly Lipschitz and S is uniformly fat (a weaker condition than convexity). Finally, we propose a generalization to the dual averaging method on the set of Lebesgue-continuous distributions over S.
Presented at the Illinois SoS Bi-Weekly Meeting, February 2015.
We rely on network infrastructure to deliver critical services and ensure security. Yet networks today have reached a level of complexity that is far beyond our ability to have confidence in their correct behavior – resulting in significant time investment and security vulnerabilities that can cost millions of dollars, or worse. Motivated by this need for rigorous understanding of complex networks, I will give an overview of our or Science of Security lablet project, A Hypothesis Testing Framework for Network Security.
First, I will discuss the emerging field of network verification, which transforms network security by rigorously checking that intended behavior is correctly realized across the live running network. Our research developed a technique called data plane verification, which has discovered problems in operational environments and can verify hypotheses and security policies with millisecond-level latency in dynamic networks. In just a few years, data plane verification has moved from early research prototypes to production deployment. We have built on this technique to reason about hypotheses even under the temporal uncertainty inherent in a large distributed network. Second, I will discuss a new approach to reasoning about networks as databases that we can query to determine answers to behavioral questions and to actively control the network. This talk will span work by a large group of folks, including Anduo Wang, Wenxu an Zhou, Dong Jin, Jason Croft, Matthew Caesar, Ahmed Khurshid, and Xuan Zou.
Presented at the Illinois ITI Joint Trust and Security/Science of Security Seminar, September 15, 2015.
Interface-confinement is a common mechanism that secures untrusted code by executing it inside a sandbox. The sandbox limits (confines) the code's interaction with key system resources to a restricted set of interfaces. This practice is seen in web browsers, hypervisors, and other security-critical systems. Motivated by these systems, we present a program logic, called System M, for modeling and proving safety properties of systems that execute adversary-supplied code via interface-confinement. In addition to using computation types to specify effects of computations, System M includes a novel invariant type to specify the properties of interface-confined code. The interpretation of invariant type includes terms whose effects satisfy an invariant. We construct a step-indexed model built over traces and prove the soundness of System M relative to the model. System M is the first program logic that allows proofs of safety for programs that execute adversary-supplied code without forcing the adversarial code to be available for deep static analysis. System M can be used to model and verify protocols as well as system designs. We demonstrate the reasoning principles of System M by verifying the state integrity property of the design of Memoir, a previously proposed trusted computing system.
Best Poster Award, ACM SIGCOMM Conference on Principles of Advanced Discrete Simulation, London, UK, June 10-12, 2015.



