 Computational Cybersecurity in Compromised Environments Workshop
Computational Cybersecurity in Compromised Environments Workshop
SoS Newsletter- Advanced Book Block
 |
Computational Cybersecurity in Compromised Environments (C3E) Workshop |

The Special Cyber Operations Research and Engineering (SCORE) Subcommittee sponsored the 2014 Computational Cybersecurity in Compromised Environments (C3E) Workshop at the Georgia Tech Research Institute (GTRI) Conference Center from 20-22 October 2014. The research workshop brought together a diverse group of top academic, industry, and government experts to examine new ways of approaching the cybersecurity challenges facing the Nation and how to enable smart, real-time decision-making in Cyberspace through both “normal” complexity and persistent adversarial behavior.
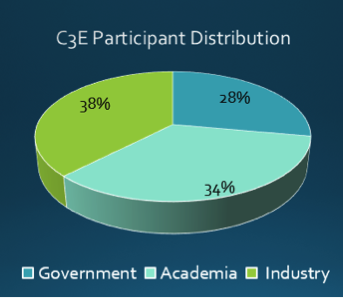
Figure 1: C3E Participation by Organizational Category
This was the sixth in a series of annual C3E research workshops, drawing upon the efforts between 2009 and 2013 on adversarial behavior, the role of models and data, predictive analytics, and the need for understanding how best to employ human and machine-based decisions in the face of emerging cyber threats. Since its inception, C3E has had two overarching objectives: 1) development of ideas worth additional cyber research; and 2) the development of a Community of Interest (COI) around unique, analytic, and operational approaches to the persistent cyber security threat.
C3E 2014 continued to focus on the needs of the practitioner and leverage past C3E themes of predictive analytics, decision-making, consequences, and visualization. To enhance the prospects of deriving applicable and adoptable results from C3E track work, the selection of the track topics, Security by Default and Data Integrity, was based on recommendations from senior government officials.
To accomplish its objectives, C3E 2014 drew upon the approaches that have been used in C3E since the beginning: 1) Keynote Speakers who provided tailored and provocative talks on a wide range of topics related to cyber security; 2) a Discovery or Challenge Problem that attracted the analytic attention of participants prior to C3E; and especially 3) Track Work that involved dedicated, small group focus on Security by Default and Data Integrity.
The C3E 2014 Discovery Problem was a Metadata-based Malicious Cyber Discovery Problem. The first goal of the task was to invent and prototype approaches for identifying high interest, suspicious, and likely malicious behaviors from metadata that challenge the way we traditionally think about the cyber problem. The second goal was to introduce participants to the DHS Protected Repository for the Defense of Infrastructure against Cyber Threats (PREDICT) datasets for use on this and other future research problems. PREDICT is a rich repository of datasets that contains routing (BGP) data, naming (DNS) data, data application (net analyzer) data, infrastructure (census probe) data, and security data (botnet sinkhole data, dark data, etc.). There are hundreds of actual and simulated dataset categories in PREDICT that provide samples of cyber data for researchers. DHS has addressed and resolved the legal and ethical issues concerning PREDICT, and the researchers found the PREDICT datasets to be a valuable resource for the C3E 2014 Discovery Problem. Each of the five groups that worked on the Discovery Problem presented their findings: 1) An Online Behavior Modeling Based Approach to Metadata-Based Malicious Cyber Discovery; 2) Implementation Based Characterization of Network Flows; 3) APT Discovery Beyond Time and Space; 4) Genomics Inspired Cyber Discovery; and 5) C3E Malicious Cyber Discovery: Mapping Access Patterns. Several government organizations have expressed interest in follow-up discussions on a couple of the approaches.
The purpose of the Data Integrity Track was to engage a set of researchers from diverse backgrounds to elicit research themes that could improve both understanding of cyber data integrity issues and potential solutions that could be developed to mitigate them. Track participants addressed data integrity issues associated with finance and health/science, and captured relevant characteristics, as shown below.

Figure 2: Characteristics of Data Integrity
Track participants also identified potential solutions and research themes for addressing data integrity issues: 1) Diverse workflows and sensor paths; 2) Cyber insurance and regulations; and 3) Human-in-the-loop data integrity detection.
The Security by Default (SBD) track focused on addressing whether secure, “out of the box” systems can be created, e.g., systems that are secure when they are fielded. There is a perception among stakeholders that systems that are engineered and/or configured to be secure by default may be less functional, less flexible, and more difficult to use, explaining the market bias toward insecure initial designs and configurations. Track participants identified five areas of focus that might merit additional study: 1) The building code analogy—balancing the equities; 2) Architecture and design—expressing security problems understandably; 3) Architecture and design—delivering and assuring secure components and infrastructure; 4) Biological analogs—supporting adaptiveness and architectural dynamism; and 5) Usability and metrics—rethinking the “trade-off” of security and usability.
In preparation for the next C3E workshop, a core group of participants will meet to refine specific approaches, and, consistent with prior workshops, will identify at least two substantive track areas through discussions with senior government leaders.
C3E remains focused on cutting-edge technology and understanding how people interact with systems and networks. In evaluating the 2014 workshop, fully 92% of the participants were both interested in the areas discussed and believed that the other participants were contributors in the field. While C3E is often oriented around research, the workshops have begun to incorporate practical examples of how different government, scientific, and industry organizations are actually using advanced analysis and analytics in their daily business and creating a path to applications for the practitioner, thus providing real solutions to address cyber problems.
(ID#: 15-5935)
Note:
Articles listed on these pages have been found on publicly available internet pages and are cited with links to those pages. Some of the information included herein has been reprinted with permission from the authors or data repositories. Direct any requests via Email to news@scienceofsecurity.net for removal of the links or modifications to specific citations. Please include the ID# of the specific citation in your correspondence.


